Proactively secure MCP Servers with Levo’s MCP Security Testing


%20(1).png)









%20(1).png)







MCP Is Accelerating AI Integration,
and Scaling Risk at the Same Rate

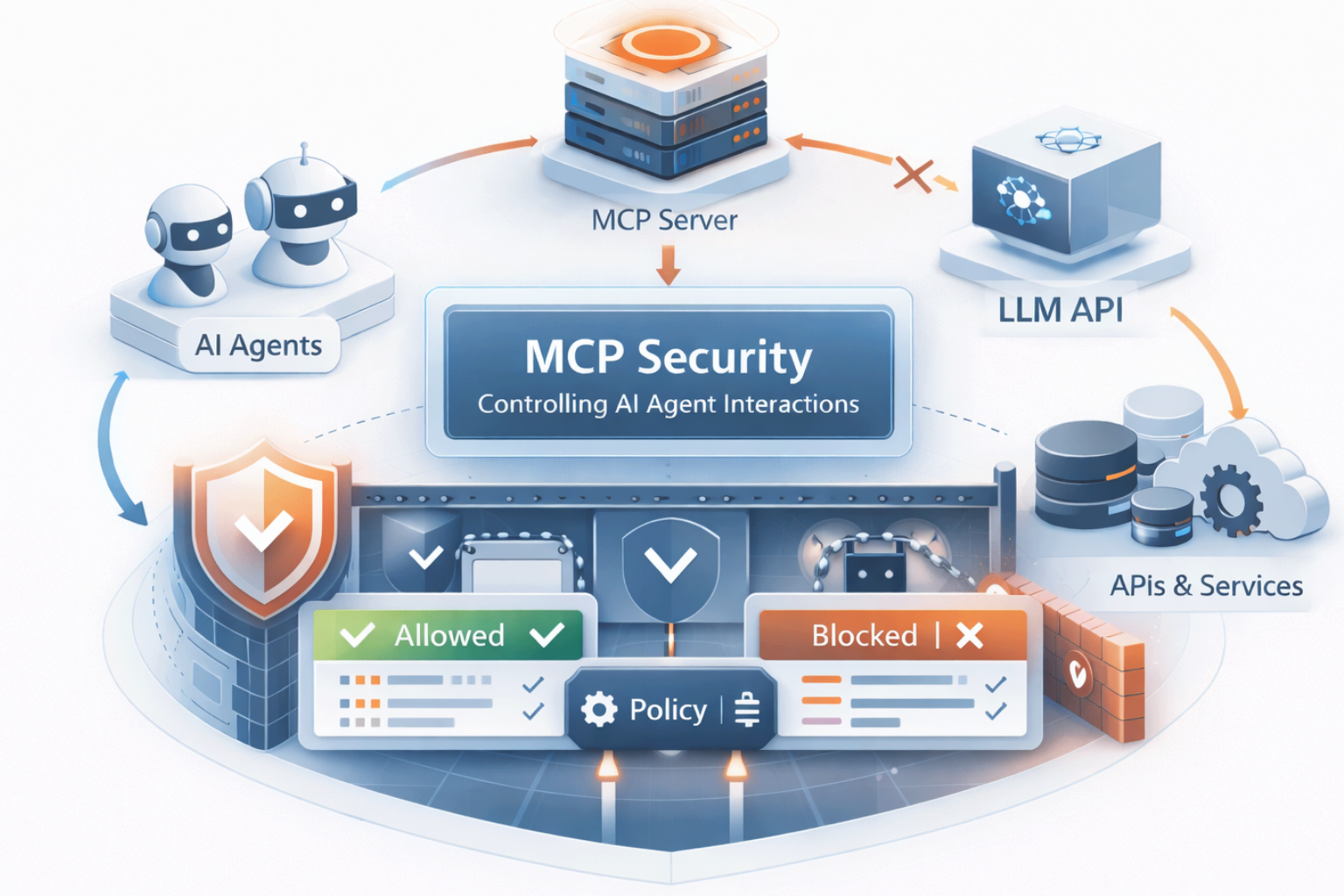
MCP servers now sit between AI and your most critical systems: repositories, databases, payment rails, and internal tools. Unlike a point-to-point integration, MCP consolidates access across multiple high-value systems through a single protocol. That consolidation is operationally efficient, but it also means that a single weak point can cascade across your entire AI-powered workflow.

Many MCP servers are created in prototype contexts, where authentication and access controls are often incomplete by design. In production, those gaps become real attack paths because MCP servers sit close to tools, data sources, and privileged actions. The consequence is not only data leakage. It is unauthorized execution through agent-tool use that looks legitimate on the surface.
.svg)
In MCP workflows, injection is not limited to “misleading responses.” It can influence tool calls, parameters, and downstream actions. That changes the risk category from content risk to operational risk. One crafted input can redirect what a server retrieves, how a tool is invoked, or what data is sent out. Without pre-production testing that mirrors real tool-use conditions, teams discover these issues only after exposure is real.

MCP makes it easy to adopt third-party servers and community tooling, which increases speed but also expands dependency risk. A single untrusted server can introduce unsafe behavior into otherwise governed AI workflows. If third-party MCP servers cannot be tested, adoption is slowed down to avoid reputational and regulatory fallout.

Traditional security testing assumes stable endpoints, slower change cycles, and clear ownership. MCP adoption flips that model. Servers appear quickly, change frequently, and spread through teams that are optimizing for shipping. Manual testing becomes a bottleneck, and partial coverage becomes the norm. That creates a cycle where security either blocks MCP adoption or accepts unmanaged exposure.

Most controls were built for predictable request-response systems and known application boundaries. MCP adds a new layer where tools, data, and actions are orchestrated through an execution protocol. Risk lives in the chain, not just in one endpoint. If security cannot test the chain as it is used, it cannot confidently approve scale. That is why MCP adoption can be simultaneously strategic and destabilizing.
Automatically validate MCP Servers
pre-production with Levo
OWASP MCP Top 10 coverage, built for MCP reality
Levo tests MCP servers against the OWASP MCP Top 10 so enterprises do not miss protocol-specific failure modes. Coverage focuses on the risks that matter in AI workflows, such as injection paths, auth failures, and data exposure. This replaces generic checklists with MCP native assurance. Security leaders get a clear basis to approve broader adoption without guessing what is untested.

No inventory required, because discovery is built in
MCP sprawl cannot be secured if it depends on teams self-reporting what exists. Levo discovers MCP servers directly so testing starts from reality, not from declarations. That removes the most common failure mode in early MCP programs: partial coverage. Organizations gain faster time-to-control without waiting for cross team alignment.

Real-world testing with real states, not lab assumptions
Levo tests MCP servers the way they are actually used, including real authentication states, real tool paths, and custom payloads that match enterprise conditions. This surfaces exploitable behaviors that synthetic tests often miss. It also reduces late-stage surprises that force rollbacks and rewrites. Engineering velocity stays high because assurance is produced under realistic conditions, not theoretical ones.

Continuous testing that keeps pace with MCP change
MCP environments change quickly as new servers appear and existing ones evolve. Levo continuously tests newly discovered servers and re-tests as posture changes, so coverage stays current. This prevents “security drift,” so MCP servers can be adopted without accumulating invisible risk.
.png)
Actionable findings only, tied to exploitability
Levo prioritizes high-fidelity findings by combining runtime and application context to reduce false positives. Alerts are designed to be acted on, not tuned endlessly. This protects scarce security bandwidth while protecting against MCP-native threats. When security output is trusted, approvals move faster and MCP adoption becomes a program, not a debate.
.png)
Reduce friction between builders, defenders, and governors of AI.

Levo validates MCP servers early, so the execution layer is proven before workflows become customer facing. That keeps release cycles predictable by removing last minute security escalations.

Levo provides continuous MCP-native testing with actionable findings, so attention stays on what is exploitable, not what is noisy. This reduces manual testing load while improving coverage across a fast-moving footprint.

Levo provides continuous test evidence and audit-ready reporting, so organizations can demonstrate that MCP servers handling customer-facing workflows meet compliance expectations.
Reduce MCP blast radius early, so AI adoption can compound.

Frequently Asked Questions
Got questions? Go through the FAQs or get in touch with our team!
What is MCP server testing?
MCP server testing is the process of validating a Model Context Protocol (MCP) server’s behavior before it is relied on in real workflows. It typically covers functional correctness, tool-call behavior, error handling, and integration reliability. Most public guidance on MCP testing focuses on debugging and functional validation. In enterprise settings, testing also needs to confirm that MCP servers behave safely under real conditions, including sensitive workflows and privileged tool paths. Levo adds the missing layer by validating whether MCP servers are safe for high-impact AI workflows before autonomous execution is trusted. Levo’s MCP Security Testing goes beyond functional checks and tests security failure modes that show up in real agent-driven usage.
What is MCP security testing?
MCP security testing evaluates whether an MCP server can be abused, manipulated, or coerced into unsafe tool execution. It focuses on MCP-specific attack paths like prompt-driven tool misuse, chained calls, token exposure, and context leakage. This type of testing validates authentication and authorization under adversarial conditions, not just happy-path behavior. The goal is straightforward: MCP servers should be proven safe before they become an execution layer inside AI workflows. Levo’s MCP Security Testing automates this validation continuously and covers common MCP risk categories so issues are found before rollout. It tests MCP servers the way they are actually used, across chained tool calls and sensitive automations.
How is MCP server testing different from MCP security testing?
MCP server testing usually means functional testing: does the server respond correctly, do tools work, and do integrations behave as expected. MCP security testing asks a different question: can the same server be pushed into unsafe behavior under realistic adversarial inputs. Functional testing often cannot detect exploit paths because it does not model malicious prompts, poisoned tool outputs, or privilege boundary failures. Security testing is what turns “it works” into “it is safe to rely on.” Levo bridges this gap by running security tests that simulate real agent usage and adversarial inputs, not only correctness checks. It keeps validation current as MCP servers and tool catalogs evolve, so security does not lag behind adoption.
What is MCP penetration testing and when is it needed?
MCP penetration testing is an adversarial assessment of MCP servers and connected tool paths to find exploit chains. It typically includes abuse case design, targeted payloads, and validation of whether weaknesses lead to real impact in real workflows. It becomes important when MCP servers can trigger high privilege actions, touch sensitive data, or run in production environments. Pen testing is also useful for high risk deployments where a single compromise would force a broad shutdown or incident response. Levo reduces reliance on purely manual pentests by continuously testing MCP servers against common failure modes at scale. Teams still get depth when needed, but the baseline validation is always on, not once per quarter.
What is MCP vulnerability testing?
MCP vulnerability testing identifies specific weaknesses in MCP servers that can be exploited. It focuses on repeatable vulnerability classes such as token leakage, authorization flaws, unsafe command execution, and context injection. The best vulnerability testing validates impact, not just detection. That means proving whether a finding can affect downstream tools, data access, or autonomous workflows, so remediation focuses on what can actually break production. Levo’s MCP Security Testing covers core MCP vulnerability classes and validates failure behavior under realistic conditions. It prioritizes actionable findings by testing with real authentication states and workflow context, not shallow scans.
What is MCP server DAST, and what does it catch?
MCP server DAST is dynamic application security testing applied to running MCP servers. Instead of scanning code, it tests the live server by sending payloads and observing runtime behavior. For MCP, DAST is valuable because many issues only show up during tool execution and chained calls. It can reveal injection paths, unsafe execution behavior, and weak access controls that unit tests or static checks often miss. Levo runs security testing against MCP servers in realistic runtime conditions, including authentication and workflow boundaries. It also supports continuous validation so new servers and changes do not silently expand the attack surface.
What is an MCP security scanner, and what should it validate?
An MCP security scanner is a tool that assesses MCP servers for security weaknesses and unsafe execution patterns. It should validate authentication and authorization, including safe failure behavior when access is denied. It should also test for prompt and context injection, because MCP servers turn language into action. It should test tool poisoning, because compromised tool outputs can quietly manipulate workflows. It should validate secrets handling, because token exposure can inherit access to downstream systems. Levo’s MCP Security Testing automates these validations and keeps them current as MCP usage evolves. It is designed to produce high fidelity findings that speed decisions, not alert fatigue.
What are the most common MCP server vulnerabilities to test for?
Common MCP server vulnerabilities include secret exposure, insecure token handling, and weak authorization boundaries. Scope creep is another frequent risk because MCP servers often gain capabilities quickly as teams iterate. Tool poisoning is a growing concern, where compromised plugins or dependencies return manipulated output that steers unsafe actions. Command injection and unsafe execution paths matter because MCP servers can generate actions dynamically. Prompt and context injection matter because attacks can be subtle and workflow dependent. Levo tests across these risk categories and maps coverage to a structured MCP focused taxonomy. This helps teams find the issues that matter before MCP becomes a production execution layer.
How should enterprises test MCP authentication and authorization?
Authentication testing should validate that tool calls cannot be invoked without valid credentials and that failure behavior is safe. Authorization testing should validate that identities cannot do more than intended, even when requests look legitimate. This testing should include denied path validation, replay attempts, and wrong identity states, not only successful calls. The goal is consistent enforcement across chained tool calls, because MCP workflows often cross multiple systems in one sequence. Levo executes tests under realistic access conditions and validates boundary behavior, so teams can expand MCP usage without expanding privilege silently. This helps approvals move faster because controls can be demonstrated, not assumed.
How does prompt injection testing work for MCP servers?
Prompt injection testing checks whether malicious instructions can override policy, extract sensitive information, or manipulate tool execution. It matters for MCP because servers translate natural language intent into tool calls, creating a direct path from text to execution. Good testing includes indirect instructions, multi step manipulation, and attempts that persist across context and tool calls. It also validates that safety holds under pressure, when prompts try to coerce the system into doing the risky thing. Levo tests MCP servers with adversarial prompts and workflow shaped manipulation attempts, not just obvious “jailbreak” strings. It is designed to preserve legitimate use while proving execution stays inside defined boundaries.
What is MCP tool poisoning, and how can it be tested?
MCP tool poisoning is when a compromised tool, plugin, or dependency returns manipulated output that steers an agent into unsafe actions. It is dangerous because poisoned outputs can look legitimate, so compromise can propagate quietly through normal workflows. Testing should inject corrupted tool outputs and misleading responses to see whether the server validates what it consumes. It should also test cross-tool chaining, where one poisoned output influences later tool calls and downstream decisions. Levo explicitly tests tool poisoning by simulating compromised tool outputs and edge case payloads. This turns “trusted plugin” assumptions into measurable proof before MCP is scaled.
How should MCP servers be tested for secret exposure and data exfiltration?
Secrets exposure testing checks whether tokens, credentials, or sensitive identifiers appear in responses, logs, caches, or error messages. It should validate token lifetimes, storage patterns, and failure behavior so accidental spills do not become persistent access. Data exfiltration testing should include context leakage across sessions and chains, because MCP workflows often persist context across steps. The desired outcome is containment, so sensitive data stays scoped to the right workflow and does not leak into tool outputs or logs. Levo approaches secret exposure like a leak hunt and validates safe failure behavior in realistic runtime conditions. It also tests boundary behavior so context cannot quietly escape into downstream systems.
How often should MCP servers be security tested?
Point in time testing catches obvious issues before deployment, but MCP risk changes as tools, permissions, and workflows evolve. MCP servers can add tools, expand scopes, or change behavior without clear “release” signals, which makes drift a predictable failure mode. Continuous testing is what keeps governance aligned with real change, not last quarter’s posture. The business outcome is stability: fewer surprises, fewer late stage rewrites, and fewer emergency pauses after an issue is found in production. Levo supports continuous validation so new MCP servers, new tools, and behavior changes do not silently expand risk. It also avoids dependency on teams self reporting inventory, which is where many programs fall behind.
What should MCP security testing produce for compliance and audit readiness?
An MCP security testing program should produce evidence of what was tested, what failed, what was remediated, and what passed. It should tie findings to specific servers, tool surfaces, and authentication states, not generic scan results. It should show that common MCP failure modes are covered and that testing aligns to a consistent taxonomy. It should also support repeatable reporting over time, because auditors and risk teams care about drift, not one successful test. Levo’s MCP Security Testing is built to generate audit ready evidence while keeping findings actionable and defensible. This reduces approval friction by anchoring risk decisions in proof rather than debate.
Show more