The most comprehensive API inventory



%20(1).png)









%20(1).png)







API visibility is the first security control
yet the first to collapse
55% of enterprises manage 500+ APIs. Still most rely on outdated methods like dev surveys, manual tags, or quarterly audits. This is why nearly 40% admit they struggle to maintain accurate inventories. With each weekly deployment this gap widens fueling blind spots security never had a chance to cover.
New APIs get deployed before security knows they exist. Deprecated ones get left online and unauthenticated. Without a real-time inventory, policy enforcement is fragmented, testing coverage is incomplete, and misconfigurations go undetected until they’re exploited. Over 60% of teams say they aren’t confident in their API inventory—so how can they be confident in their controls?
Attackers don’t bypass security defenses, they walk through backdoors like shadow and zombie APIs. These endpoints evade security baselines, logging and monitoring giving attackers an entry point into systems.Tools miss them, Teams forget them, which is why attackers exploit them first.
API discovery that powers coverage
Currently only 15% of enterprises feel confident in their API Inventories despite spending countless developer quarters on them. Levo’s API Inventory Portal ensures that you have full confidence and context into your API Ecosystem.
Every API catalogued so none slip security scrutiny
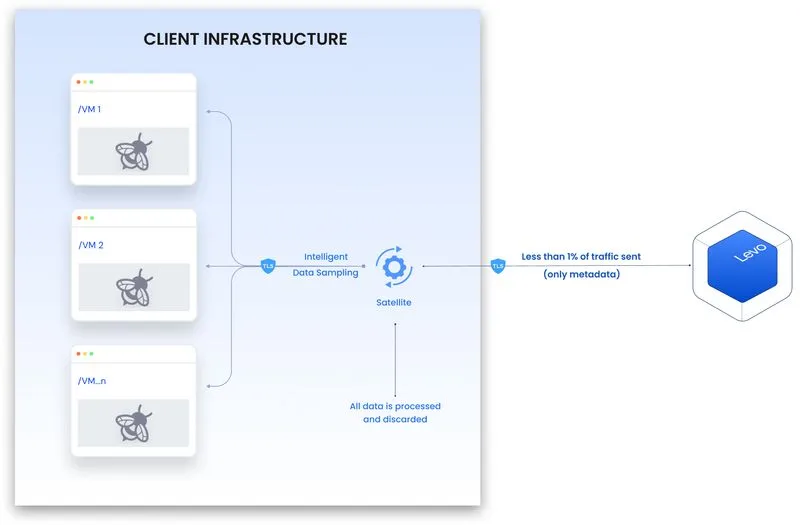
Levo’s eBPF-powered sensor and 12+ agentless techniques continuously discover every API in your ecosystem: internal, external, partner, open-source, third-party, shadow, and zombie across dev, QA, UAT, staging, SIT, and production.
Our discovery spans all frameworks, languages, and API types without requiring code or config changes. As new APIs are added via commits or integrations, your inventory auto-updates and alerts are triggered in real time.
%20.webp)
Environment specific inventory with full behavioral context
Levo doesn’t just list APIs it understands how each one behaves. Our discovery engine captures and records key runtime parameters per environment, including:
1. Authentication Status
2. Rate Limiting Status
3. Version history
4. Error response handling
.webp)
Risk context for every endpoint, prioritized and actionable
Levo flags endpoints with sensitive data exposure and weak or missing authentication, so remediation efforts can be prioritized towards endpoints who need them the most.
Endpoints are grouped by AuthN scheme, letting you audit deviations from policy at a glance across environments.With Levo’s trace-level filtering, teams can isolate endpoints by path, method, or status code spotting usage patterns and misconfigurations that signal silent risks before they become incidents.
.avif)
One API inventory portal to
align security

Enterprise-wide API Visibility that accelerates builds, integrations and reuse without extra manual work.

Real time visibility to detect risks, prioritize security testing and monitor changes without chasing dev teams.

Always up-to-date asset records and exportable reports without manual audits, interviews and checklists.
Get the security bedrock right, not just step one.

Frequently Asked Questions
Got questions? Go through the FAQs or get in touch with our team!
What is API Inventory?
Levo’s API Inventory is a continuously updated, behavior-aware map of all APIs across your environments. It’s not just a list, it’s a real-time foundation for enforcing security controls, meeting compliance mandates, and accelerating secure development because enterprises can't secure what they can't see.
Why is keeping an API Inventory important?
You can’t secure what you don’t know exists. Without a reliable inventory, critical APIs may remain unmonitored, unauthenticated, or misconfigured, becoming easy targets for attackers. Inventory gaps also lead to incomplete testing, failed audits, and policy enforcement blind spots.
How can API Inventory be maintained?
Traditionally, API inventories are built through manual tagging, dev surveys, or quarterly audits but these are error-prone and quickly outdated. The only sustainable way is through continuous, automated discovery that keeps pace with CI/CD and cloud sprawl.
How does Levo solve the API Inventory problem?
Levo uses a powerful eBPF-based sensor and over 12 agentless techniques to continuously discover and catalog every API internal, external, shadow, zombie, third-party across every environment. It requires no code or config changes and updates in real time as APIs are deployed or changed.
How is Levo better than other solutions available in the industry?
Most tools rely on static scanning, documentation parsing, or traffic sampling with limited visibility. Levo offers behavior-aware, context-rich, and environment-specific API discovery. It doesn’t just list APIs, it understands how they behave, what risks they pose, and who owns them.
What kinds of APIs does Levo discover?
Levo automatically detects internal, external, partner, third-party, open-source, shadow, and zombie APIs across REST, GraphQL, gRPC, and SOAP protocols. Even rarely used or low-traffic endpoints are surfaced and monitored.
How does Levo discover shadow and zombie APIs?
Levo combines code-based instrumentation with traffic analysis to uncover both unused or undocumented APIs in your codebase (shadow/zombie endpoints) and validate their runtime behavior. This dual approach ensures even rarely called or inactive endpoints are surfaced before attackers exploit them.
What makes Levo’s inventory “smart” or behavior-aware?
Each API in Levo’s inventory is enriched with metadata like authentication scheme, rate limits, status codes, version history, and sensitive data exposure. Teams can filter or group APIs based on behavior, making it easier to prioritize risk and streamline security testing.
How does Levo keep its API inventory continuously updated?
Levo detects new APIs as they’re deployed or integrated. Version history is tracked automatically, and changes are flagged in real time. This prevents drift between environments and keeps security and compliance aligned with what’s actually running.
How does Levo discover APIs without requiring code changes or developer time?
Levo captures API traffic directly at the kernel layer using eBPF sensors, completely out-of-band. This passive, pre-encryption visibility requires no code changes, no config edits, and no developer involvement. For restricted environments, Levo supports agentless, log-based, and file-based ingestion methods.
Which platforms does Levo integrate with?
Levo is platform-agnostic and supports all major environments including dev, staging, UAT, SIT, and production across hybrid, multi-cloud, and containerized infrastructures. It integrates seamlessly into CI/CD pipelines, observability platforms, and developer workflows.
How is Levo’s API inventory different from existing tools?
Levo's inventory is built from live runtime behavior, not stale snapshots or user-submitted specs. It includes rich metadata like auth schemes, rate limits, version history, and error behavior and flags risks in real time, enabling action, not just visibility.
Does Levo track APIs across different environments?
Absolutely. Levo offers environment-specific visibility, meaning you can track how APIs behave differently across dev, staging, production, and other environments providing accurate context for prioritization, testing, and risk reduction.
How does Levo help with compliance audits?
Levo provides exportable, always-updated records of API assets, auth posture, data exposure risks, and testing coverage eliminating the need for manual interviews, spreadsheets, or last-minute scrambles during compliance cycles.
Does Levo provide risk context for each API?
Yes. Each API is enriched with actionable risk signals such as exposure of sensitive data, missing authentication, or inconsistent rate limits so security and compliance teams can prioritize efforts intelligently.
Will developers need to tag or declare APIs manually?
No. Levo requires zero developer intervention to detect, tag, or declare APIs. Everything is automatically discovered and contextualized so developers stay focused on building, not inventory maintenance.
Show more