Levo solves the problem
without creating new ones
Most other application vendors barely secure applications but introduce
Vendor-induced security risks
Compliance complications
Large Increments in cloud bills


%20(1).png)









%20(1).png)








Levo cuts cloud bills and TCO without cutting corners
All of Levo’s modules run on just 0.5 vCPU and 0.5GB RAM - even in the most demanding production environments.

We process <1% of traffic in our SaaS, saving enterprises $100,000 to $500,000 annually in egress and cloud costs.

We achieve this by sampling only what matters, processing it locally, and discarding traffic after analysis.

No terabytes of duplication. No expensive mirroring. No noisy instrumentation slowing pipelines.

Our flexible config and optimization beat API security modules retrofitted onto edge-based architectures.

Levo was engineered from the ground up to be precision-oriented, not brute-force dependent.


Everyone else secures APIs in parts
Levo secures the whole SDLC
Levo doesn’t just promise data security, it’s designed for it.
Levo never ingests PII, PHI, or customer payloads, less than 1% of customer data (only Open API Specs and metadata) enter our SaaS.
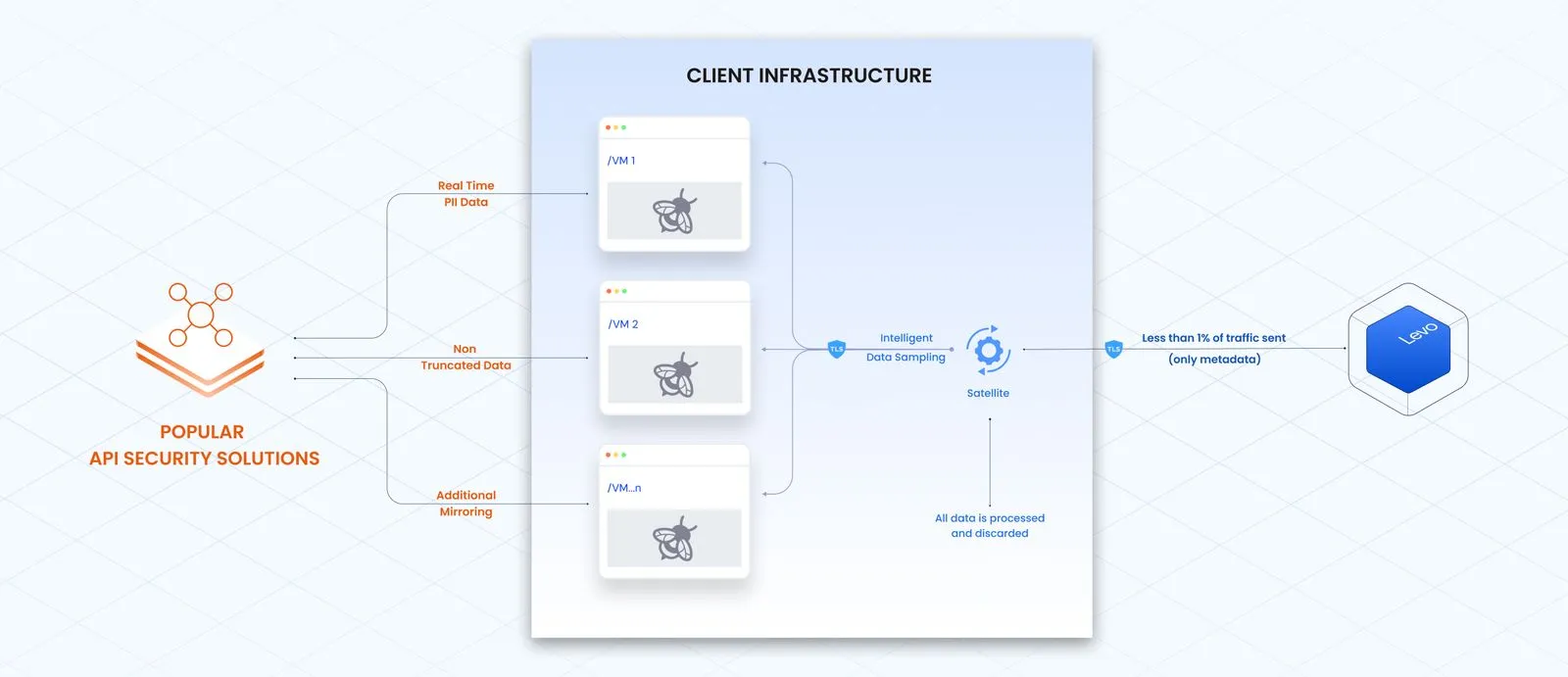
We achieve this by separating traffic capture from traffic processing. Both layers can be fully self-hosted without losing functionality.
Unlike tools that ingest full payloads and attempt redaction after the fact, we remove sensitive values at the source.
Making Levo deployable in highly regulated sectors: BFSI, healthcare, and critical infra.
We don’t induce redlines, DPIAS, or compliance violations because no sensitive data ever leaves your environment.
Loved by industry analysts, practitioners and consultants
We didn’t join the API Security Bandwagon. We pioneered it!

.png)
.png)
.svg)


