Ship open banking APIs rapidly


%20(1).png)









%20(1).png)







Share customer data responsibly with secure by default APIs
Secure third party provider (TPP) onboarding without core exposure
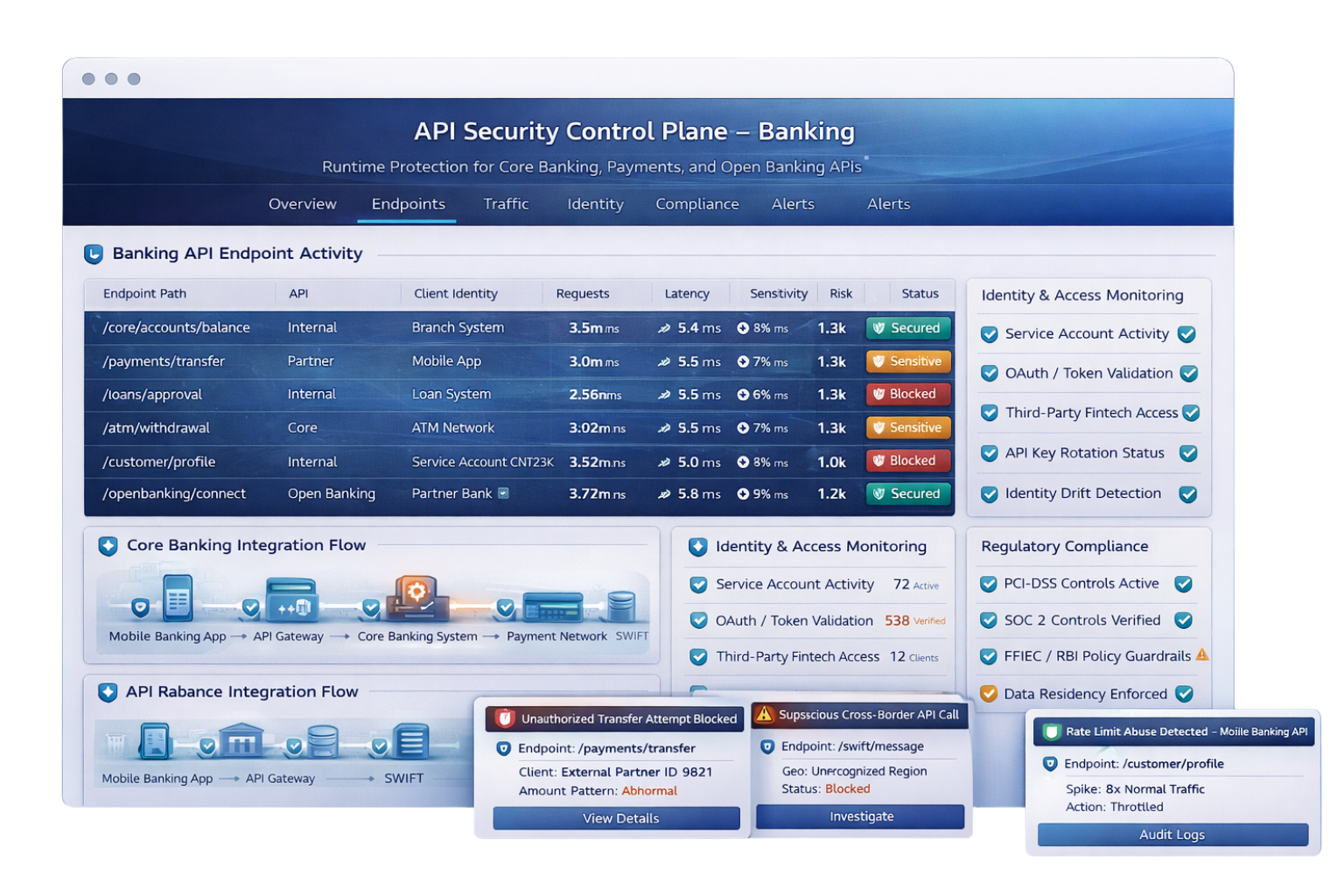
Discover every API exposed to TPPs, monitor what data they access, enforce consent boundaries automatically, and spot unsafe access patterns.
Continuous consent lifecycle enforcement and visibility
Monitor active token scopes, enforce real-time consent expiration, bind sessions to verified user intent, and revoke access instantly at the authorization layer, not just at the client.
Embed financial grade API security before deployment, not after breach
Automate vulnerability testing for OAuth flows, consent scope drift, PKCE enforcement, token reuse attacks, and FAPI-mandated control points directly inside CI/CD pipelines.
Demonstrate continuous security maturity to earn trust and approvals
Export real-time API security coverage, governance validation, sensitive data protection mapping, and compliance-ready audit artifacts mapped to PSD2, FAPI, GDPR, GLBA, and PCI-DSS.

Embrace open banking
securely with Levo
Continuous visibility across core, sandbox, and TPP ecosystems
Levo automatically discovers every API in your environment: published, sandbox, internal, or deprecated mapping endpoints to risk categories like payment initiation or data aggregation without requiring code changes. Instead of fragmented inventories, banks gain a live, centralized view of all exposed APIs before attackers or auditors find the gaps.
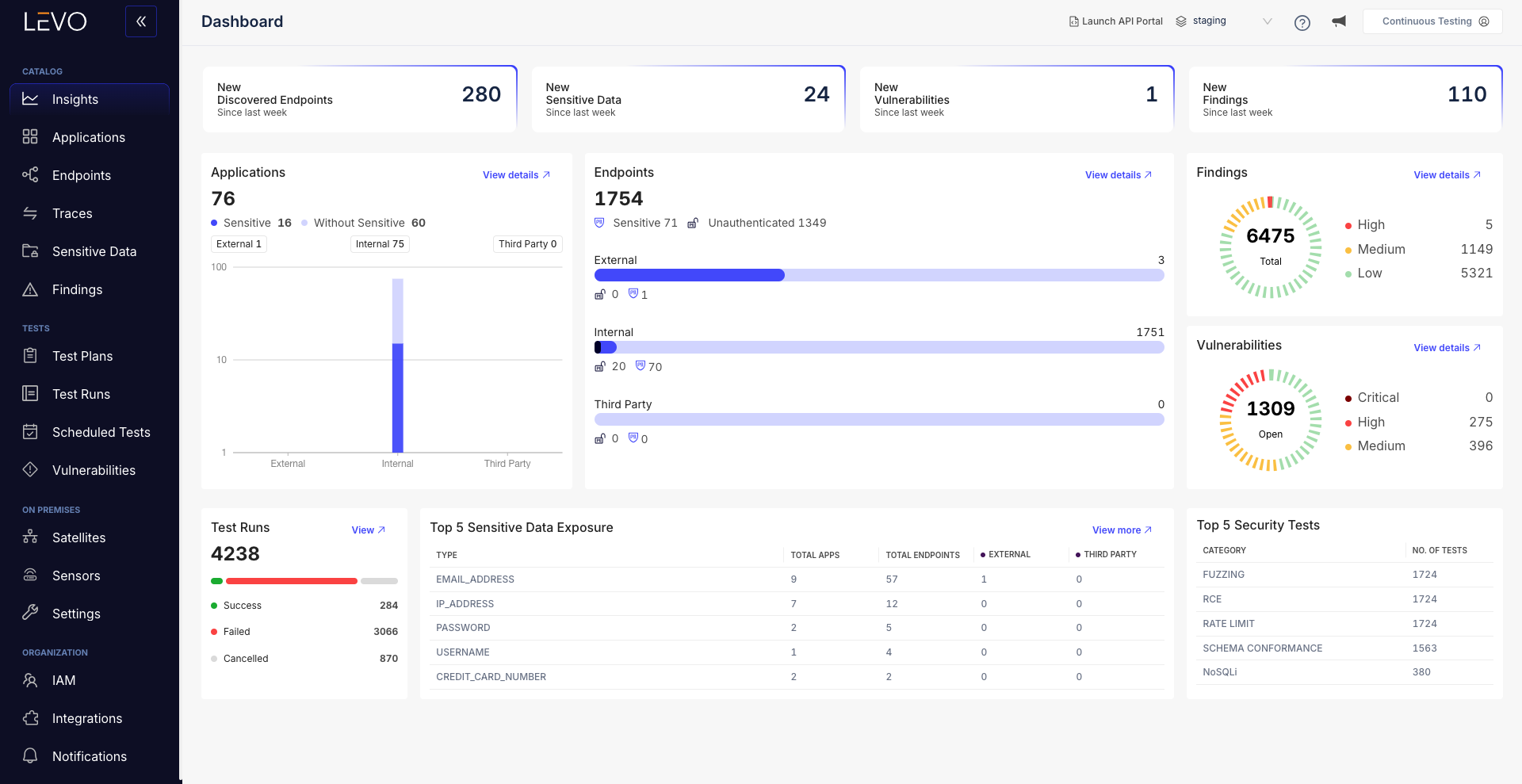
Automated API documentation for rapid integration
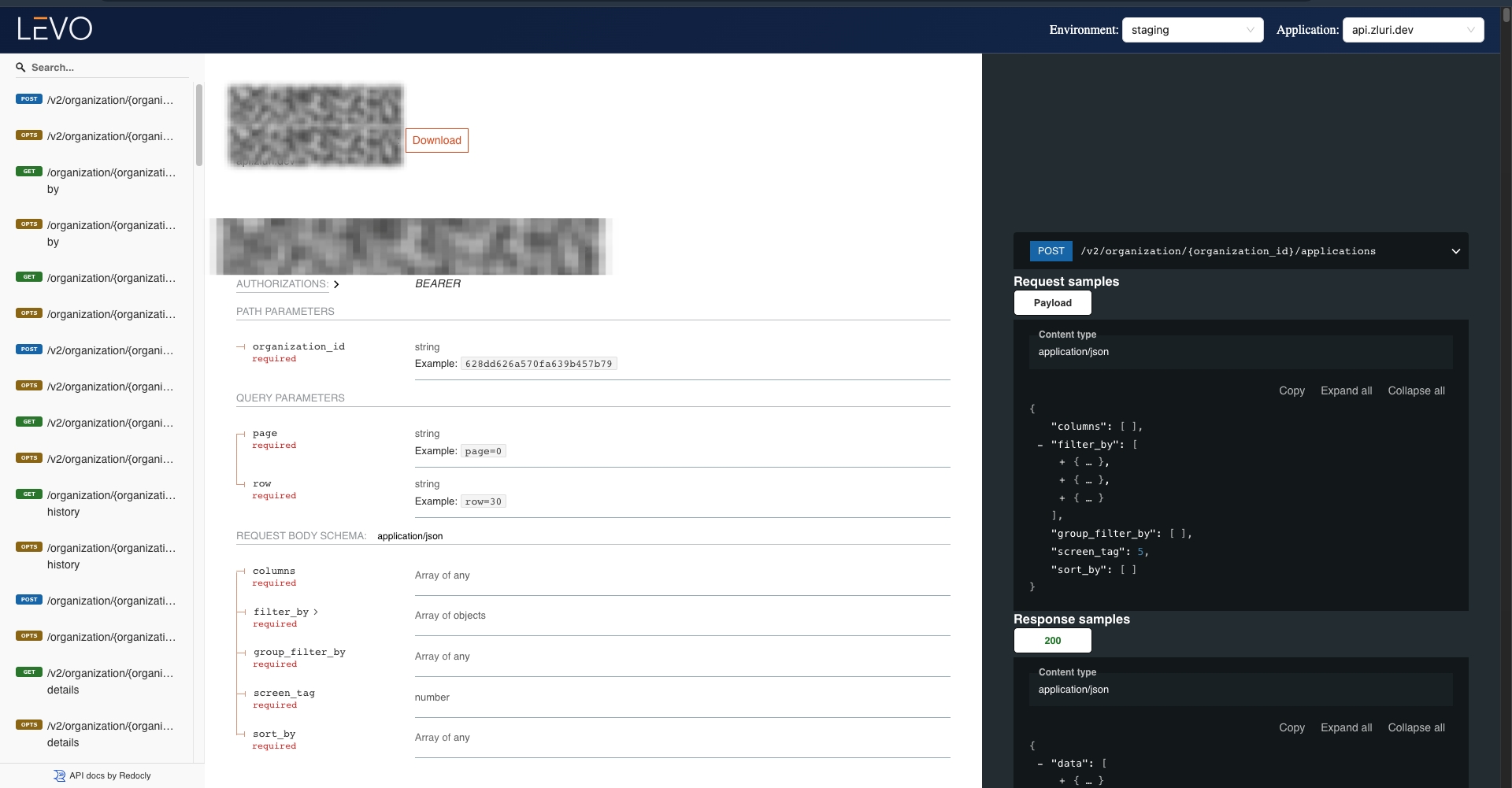
Every discovered API is auto-documented with 12+ critical parameters including versioning, response structures, AuthN logic, and rate limits enhanced with human-readable descriptions that accelerate third-party fintech onboarding.
Levo removes the manual bottleneck in integration handoffs and creates exportable artifacts banks can directly submit for PSD2, GDPR, and PCI audits.
Sensitive data mapping and exposure prevention
Levo continuously analyzes API payloads to detect and classify sensitive data flows covering PII, account metadata, transaction details, and consent flags across all environments and integrations, even third-party APIs.
This ensures banks can enforce access controls where they matter the most and reduce customer compliance risks.

Financial grade security testing embedded into CI/CD pipelines
Every API version, new endpoint is subjected to real-world attack simulations for BOLA, BFLA, OAuth scope escalation, and JWT replay vulnerabilities so standards like phantom tokens, PKCE and signed payloads are met.
Testing is natively embedded into CI/CD pipelines like GitHub Actions and GitLab, allowing banks to maintain secure release velocity without sacrificing compliance.

Continuous API monitoring to prevent violations
Levo monitors API traffic across production and sandbox environments for deviations from security baselines.SSL inconsistencies, missing headers, leaked server versions, unencrypted traffic, PII overexposure, and over 50 other misconfigurations are flagged.
Custom rules in YAML or Python enable banks to adapt detection to evolving regulatory demands without rebuilding in-house monitoring.

Shift left without breaking developer flow




