Drive secure, scalable
agentic productivity


%20(1).png)









%20(1).png)







Agentic workflows are not reaching their fullest potential
because infras was an afterthought

AI agents and copilots are blocked from accessing traces, test outcomes, and authentication states. Without this context, they can’t validate fixes, triage vulnerabilities, or take meaningful action within enterprise workflows.

42% of enterprises need eight or more integrations just to get agents functional inside production environments. Each new interface expands the attack surface without unified access control, exposing sensitive data paths before security teams can enforce policies.

Teams build brittle wrappers around LangChain or vector DBs in an attempt to sync context across agents. But these systems weren’t designed for versioned memory, multi-agent collaboration, or governance leading to fragility at scale.

Most teams still can’t see what an agent knows, remembers, or shares. Without trace-linked observability or memory introspection, debugging becomes guesswork and incident response loses valuable time.

Agent memory layers lack encryption, RBAC, and auditability. Security teams are excluded from oversight, making it impossible to enforce policies, validate outputs, or unblock AI adoption in regulated environments.

Gartner notes that AI adoption success depends on access to well-structured, governed data yet as Deloitte highlights this Normalization layer is missing.
Teams are forced to manually, extract, correlate and interpret data instead of having a telemetry that by default produces actionable and real-time insights. Humans can still reason across disconnected logs and dashboards, but AI agents can’t infer structure from entropy, stalling without explicitly defined traces, schemas, and access paths.
Application delivery timelines
shrunk in half
MCP offers two programmable primitives:
Resources to query for scoped context and Tools to trigger secure, bounded actions.
Faster innovation cycles without compounding security risks
AI agents and internal teams can now act on Levo’s live, evolving security knowledge graph without manual coordination or UI delays. This unlocks autonomous triaging, remediation, and verification within terminals, copilots, and pipelines.
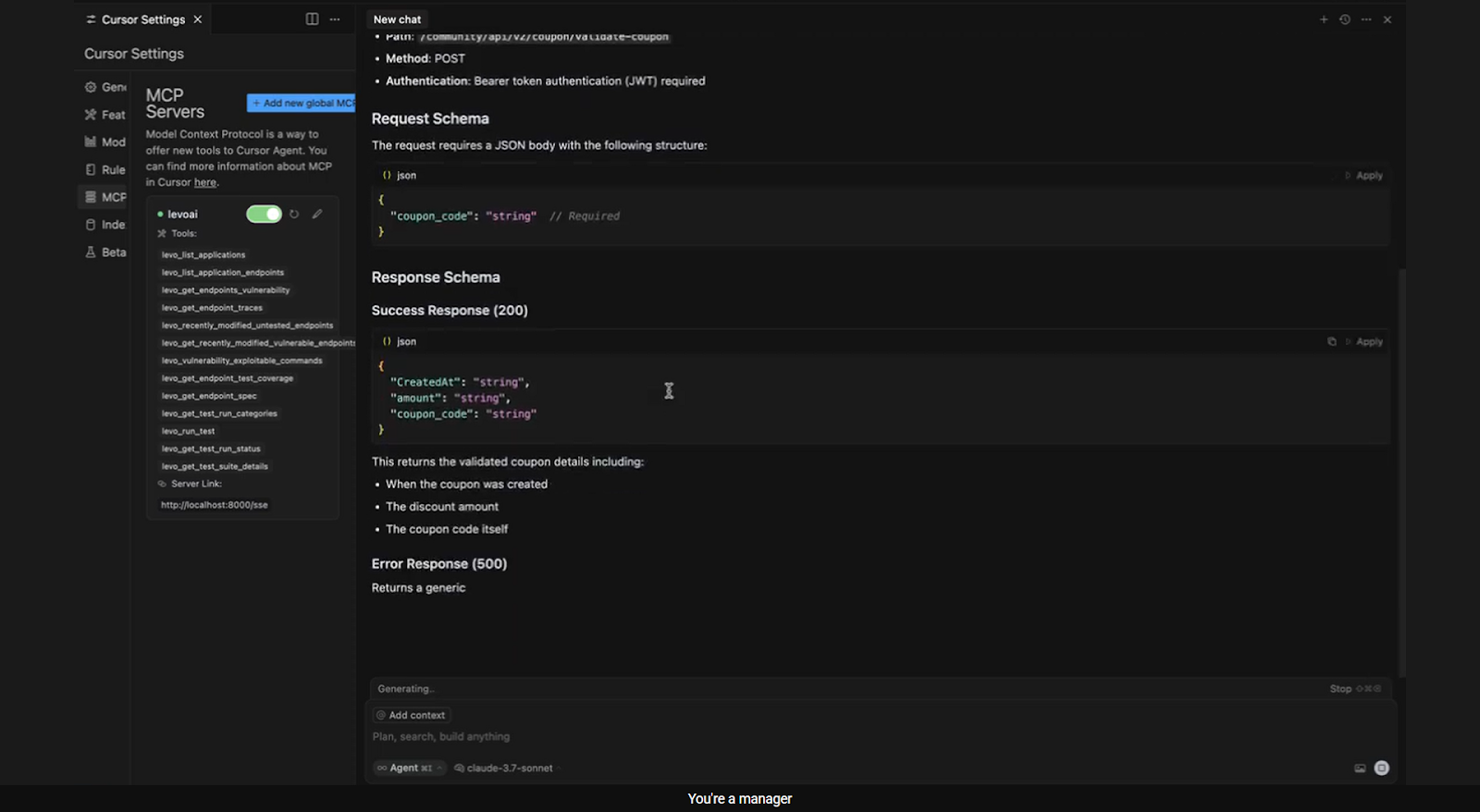
Full visibility into security coverage without UI dependency
Levo makes test outcomes, exploit traces, and untested endpoint data queryable across environments. Engineers and agents don’t need to rely on portal access or Slack threads to understand what’s missing. Security Posture is always up-to-date, triagable, and available on-demand.
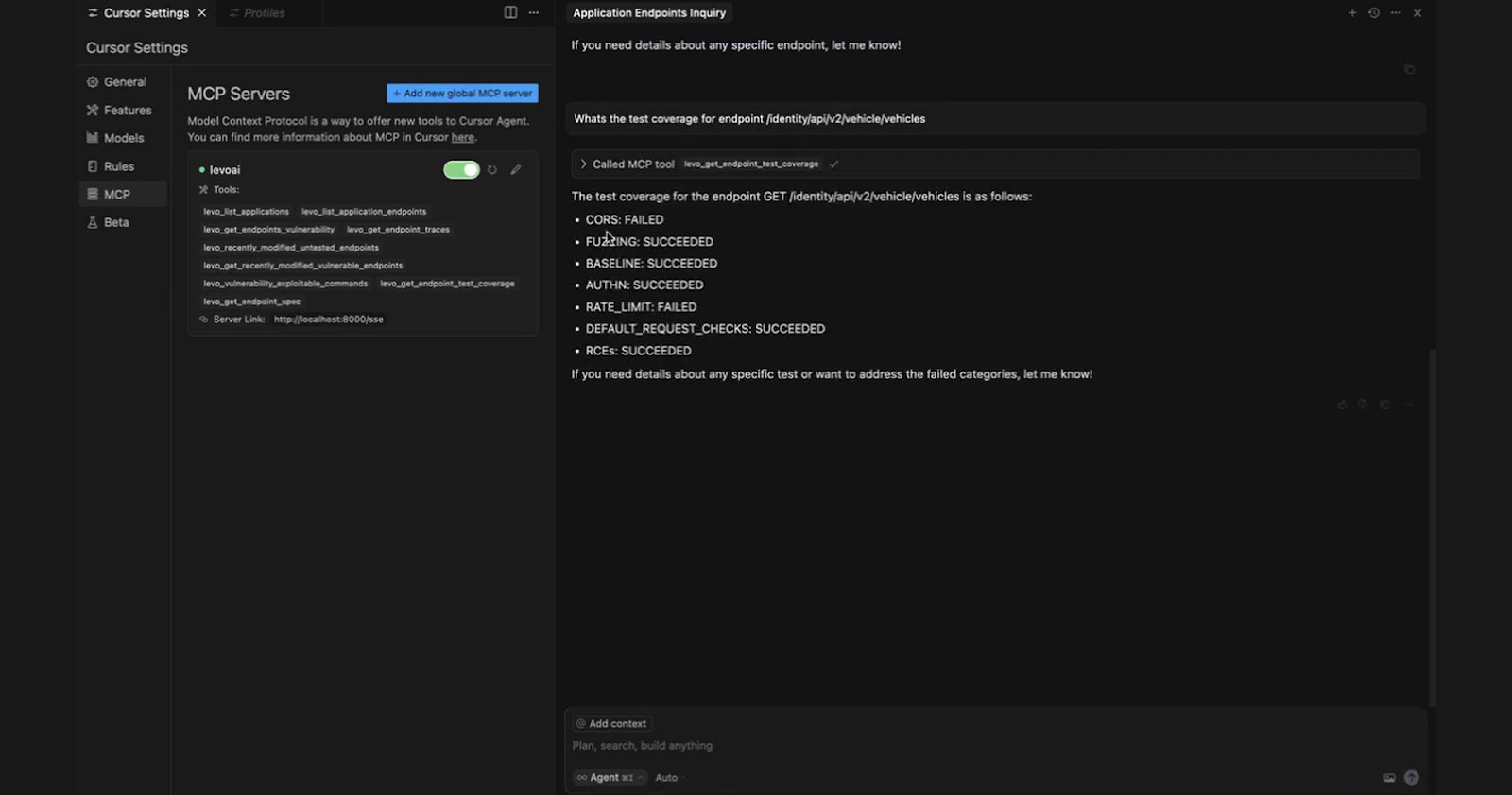
Infinitely better testing coverage without additional budget
Non-technical users and AI agents can re-run failed tests, generate variant payloads, and simulate follow-up attacks all from within their IDEs or terminals. Testing becomes continuous, composable, and integrated into everyday workflows.
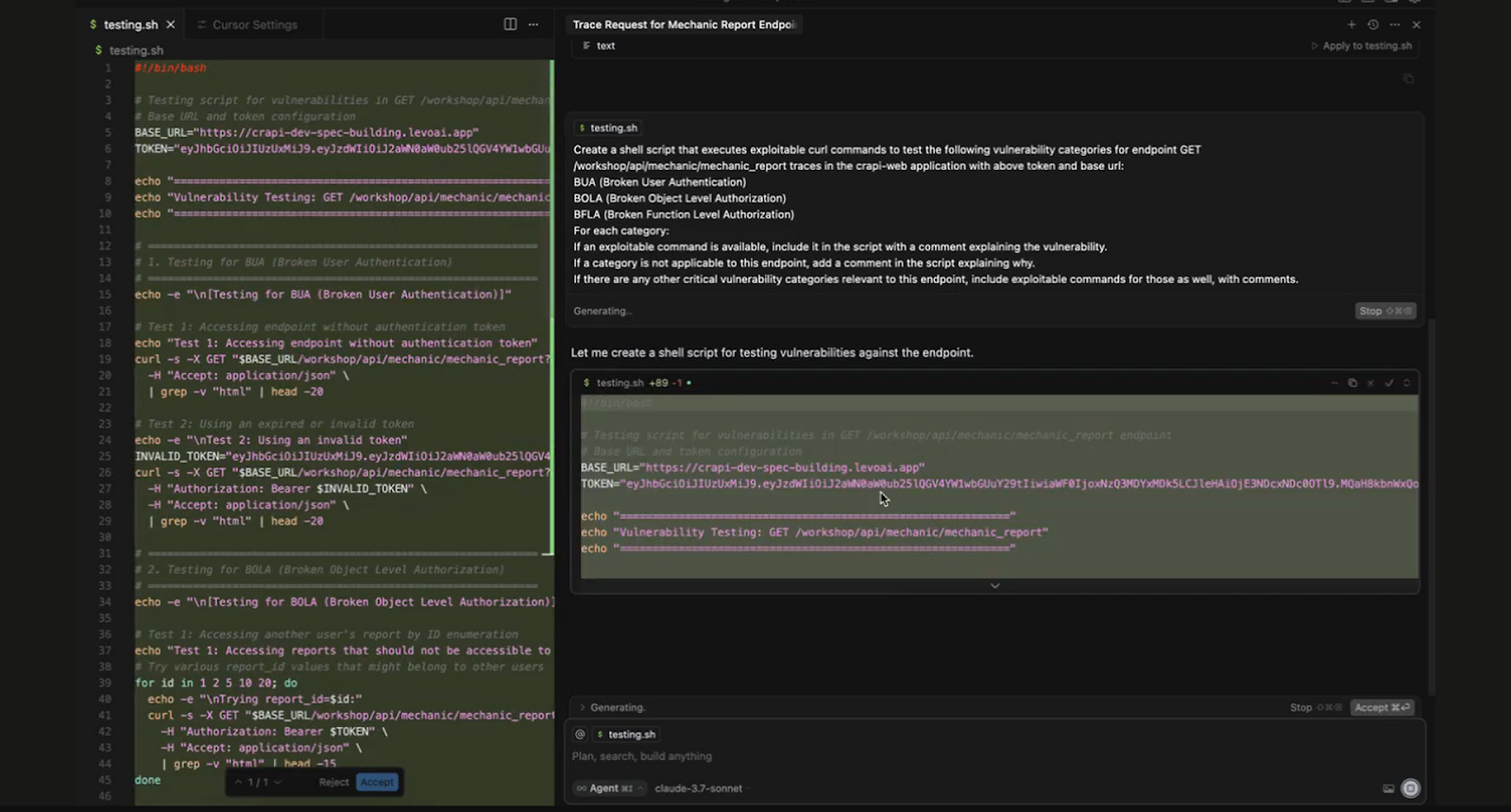
Every team wins when security intelligence is programmable

Eliminate repetitive new hire walkthroughs and accelerate secure fixes by providing engineers with live, context-aware, and auto-generated remediation code they can trust.

With programmatic access to Levo’s knowledge graph, SecOps teams can automate deeper, context-rich tests and streamline triage, all while avoiding unnecessary headcount expansion or tool sprawl.

Custom, audit-ready evidence on demand as MCP can create reports in the exact structure each framework requires, so it's not evidence creation that's automated but also evidence assembly.
Runtime security intelligence without the human, UI or security gatekeepers

Frequently Asked Questions
Got questions? Go through the FAQs or get in touch with our team!
What is MCP server?
Levo’s MCP Server is a governed, programmable API layer that exposes real-time, runtime-aware API security insights to developers, agents, and internal tools—without UI or human dependency.
Why is MCP server important?
Without it, AI agents and internal teams operate on stale or disconnected context. MCP makes Levo’s live security graph accessible, enabling safe, automated action within DevSecOps and agentic workflows.
How is Levo’s MCP server better than other MCP solutions available in the industry?
Unlike generic memory layers, Levo’s MCP is grounded in live API telemetry, not static snapshots. It’s purpose-built for secure, programmable access to real exploit traces, auth states, and test outcomes.
How does Levo’s MCP server help AI agents and copilots?
It turns agents from observers into secure operators by giving them real-time access to security posture, test results, and trace data enabling them to triage, rerun tests, and validate fixes without supervision.
What makes Levo’s MCP server secure enough for agent access?
All data surfaced via MCP is scoped, versioned, RBAC-controlled, encrypted, and audit-logged ensuring agent workflows are compliant and contained by default.
Is Levo’s MCP server real or batched?
MCP is real-time. Queries return live, correlated security data directly from Levo’s continuously updated API knowledge graph.
What actions can be triggered via Levo’s MCP today?
Agents and engineers can rerun failed tests, generate payload variations, fetch exploit traces, or query test coverage and data exposure across environments directly from their terminals or copilots.
Do I need to modify my agents or pipelines to use Levo’s MCP?
No. MCP exposes standardized, language-agnostic primitives that work with existing IDEs, LLM agents, or internal tools, no rewrites or custom wrappers required.
Can Levo’s MCP help during compliance or audit checks?
Yes. Compliance teams can query jurisdiction-specific data (e.g., Aadhaar endpoints without MFA), export reports, and generate evidence-backed responses without pulling dev or security teams off-task.
Show more