Retain the revenue your APIs create


%20(1).png)









%20(1).png)







Software has evolved: API-first
security hasn’t kept up.

SAST and DAST weren’t designed to discover or test APIs. They rely on predefined endpoints or static code views and can’t detect runtime behavior or chained API logic. WAFs only inspect and block traffic at the edge, reinforcing a reactive model that misses internal APIs, business logic abuse, and data exposure.

Legacy tools generate thousands of uncorrelated alerts without exploitability, runtime context or prioritization. Security teams are stuck triaging theoretical issues while real vulnerabilities go unnoticed, unresolved and live.

Most enterprises test only their most visible APIs, and usually just once or twice a year. Which is as good as testing none since even a single unauthenticated or misconfigured API can cause privilege escalation, data exfiltration, or full lateral compromise.

Manual testing and outdated scanners delay releases, break pipelines, and frustrate developers. Static scans with high false positives force teams to choose between security debt and deployment delays—often leading to bypasses and blame-shifting rather than true shift-left adoption.
Never choose again between
depth again
Security that matches your dev velocity not undermines it
Levo generates 1000+ customized payloads per endpoint using API Documentation, API Catalogue and detects sensitive data flows. These tests cover OWASP API Top 10, MITRE, NIST API Guidelines, injection flaws, business logic abuse, insecure configurations, and across every new commit, change, or integration automatically and continuously.
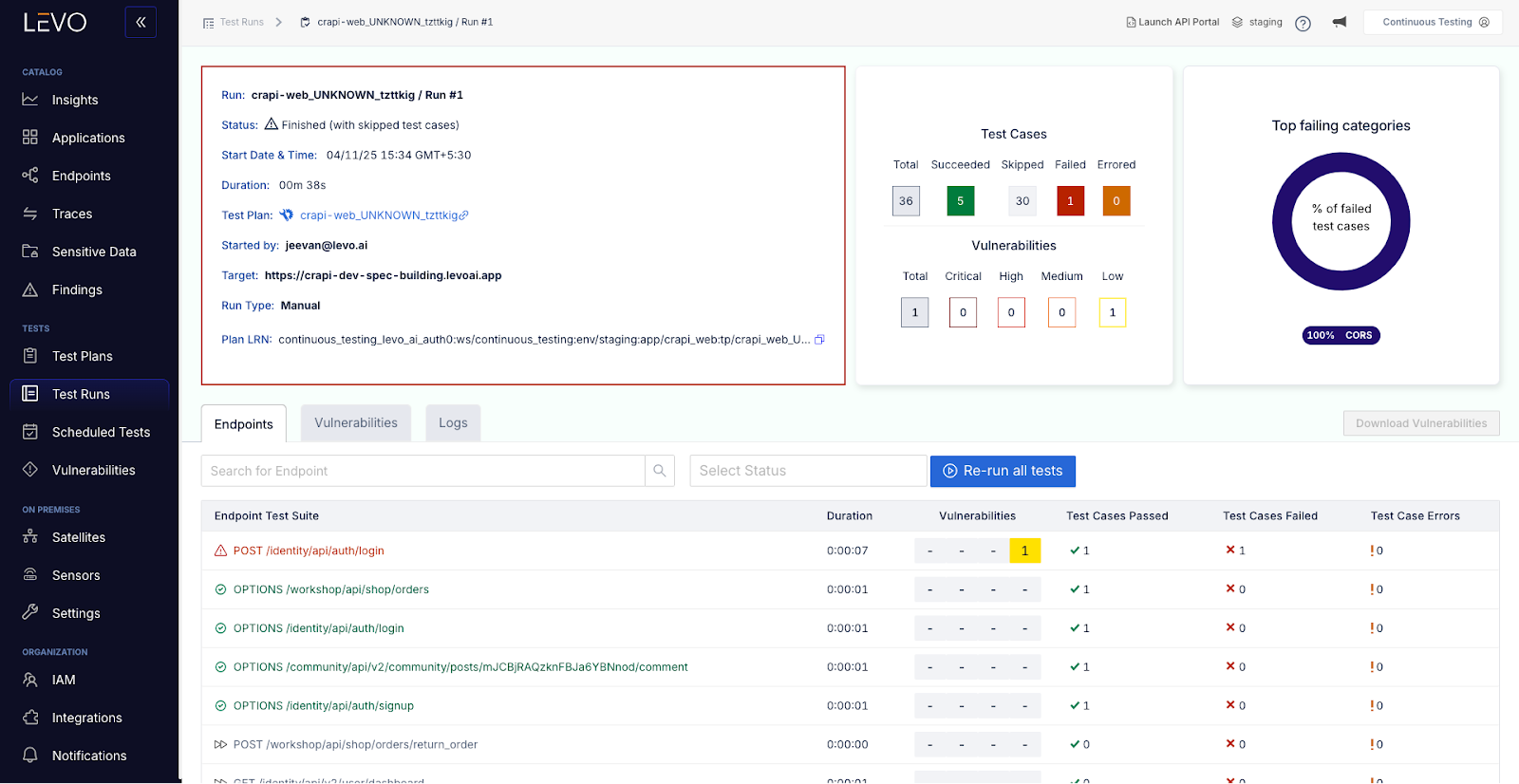
No more token errors or skipped endpoints. AuthN is handled automatically
Levo auto-detects each API’s authentication scheme OAuth2, JWT, mTLS, API keys and dynamically manages token generation, injection, renewal, and expiry. This eliminates brittle scripts and failed tests caused by expired or missing tokens.
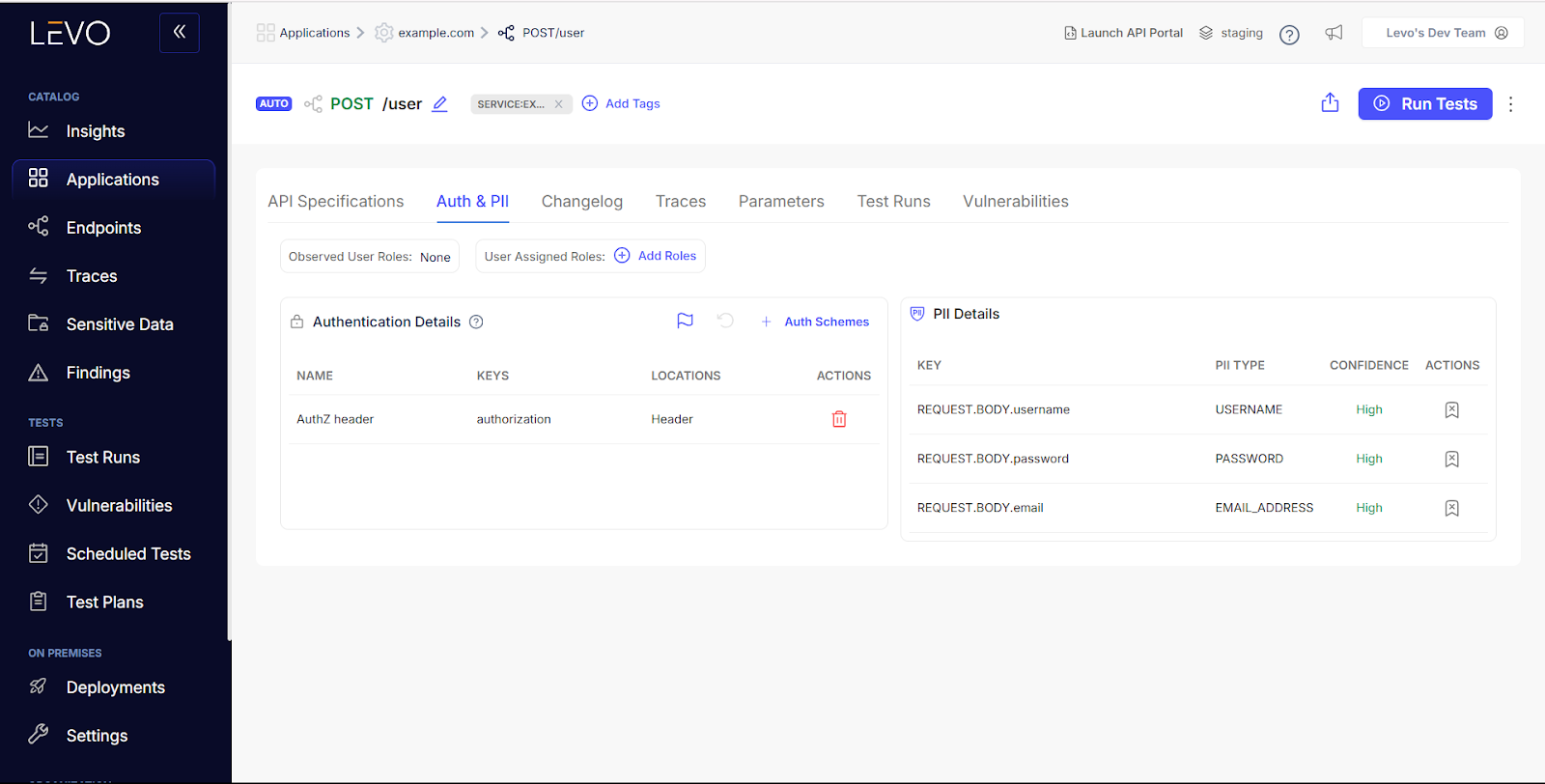
Simulated exploits that reflect real world behaviour not assumptions
By mapping API traffic to real users and roles, Levo builds payloads that reflect actual usage and abuse paths enabling accurate testing of BOLA, broken AuthZ, and permission escalation scenarios. The result, deeper test coverage without manual tuning.
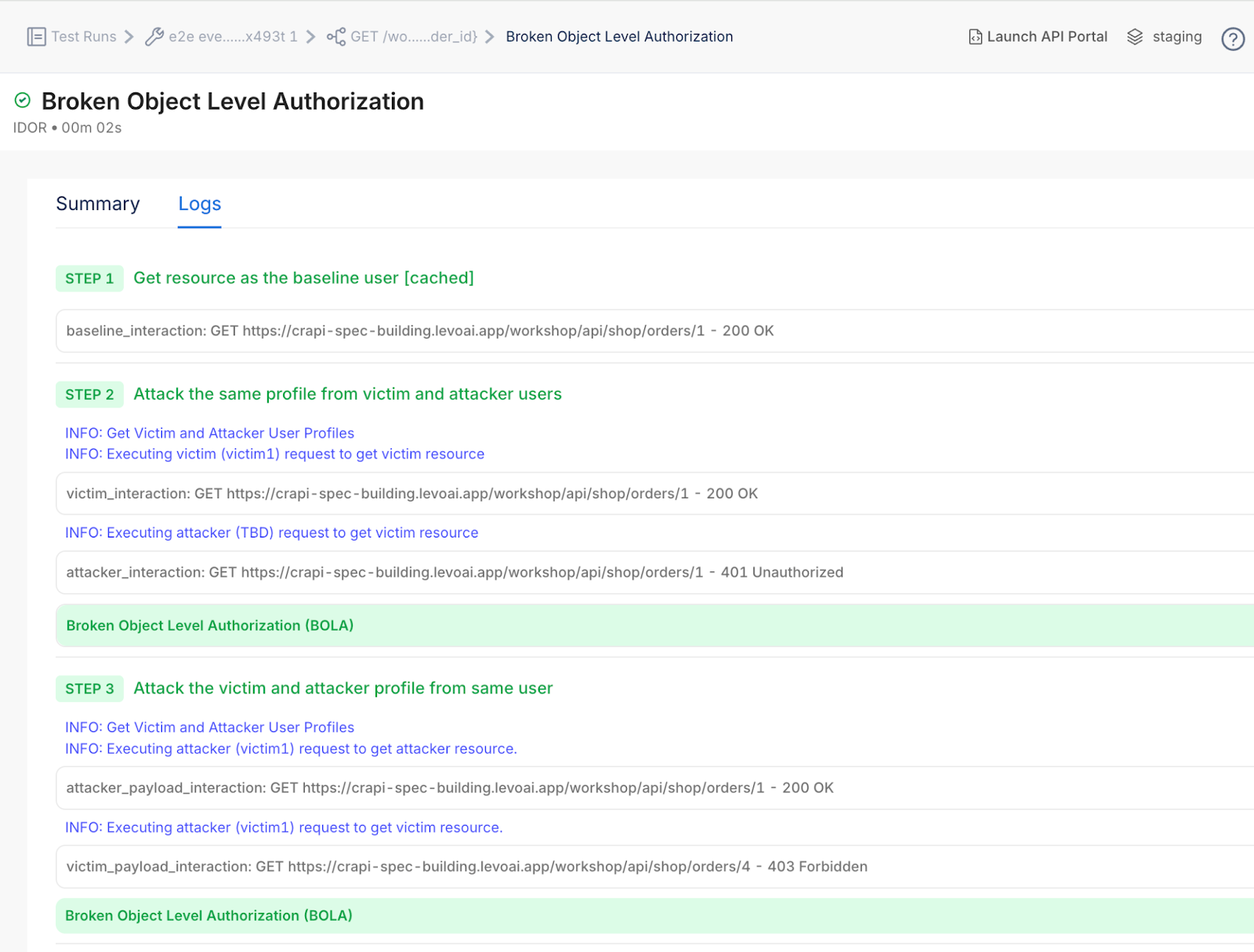
Faster builds, fewer breaches, smoother audits

Developers launch faster as APIs are secured automatically turning velocity into sustainable business expansion, not risk

Levo ends the triage grind and frees security to remediate what matters, strengthening security posture with every release.

Effortless Compliance success instead of reperforming posture for every audit because security is done right from day one.
The security testing your APIs need. At the depth, frequency and speed they deserve

Frequently Asked Questions
Got questions? Go through the FAQs or get in touch with our team!
What is API security?
API security refers to the protection of APIs from abuse, exploitation, and misconfiguration. It ensures that APIs are only accessed and used as intended by the right users, with the right permissions, at the right time.
Why is API security important?
APIs now power most digital services and account for the majority of application traffic. A single vulnerable API can lead to data leaks, compliance violations, and full-scale breaches putting revenue, reputation, and customer trust at risk.
How is Levo better than other solutions available in the industry?
Levo combines the depth of pen-testing, the breadth of automation, and the speed of CI/CD-native tools without requiring code changes, scripting, or manual triage. It tests 100x more APIs than pen tests and only surfaces real, exploitable vulnerabilities.
What makes Levo different from traditional security testing tools?
Traditional tools like SAST, DAST, and WAFs miss runtime behavior, role-based access flaws, and internal APIs. Levo uses real traffic, live context, and simulated exploits to catch what legacy tools can’t before production.
Does Levo replace or complement our existing pen testing or scanners?
Levo complements existing tools by closing critical gaps. While scanners and pen tests may still be used for compliance snapshots, Levo ensures continuous, context-aware testing for all APIs across every environment.
Can Levo test internal APIs and staging environments?
Yes. Levo tests both internal and external APIs across dev, staging, UAT, and production using its eBPF-based sensor and CLI or SaaS platform. You’ll never risk hiding behind the firewall again.
How does Levo handle authentication across APIs?
Levo auto-detects OAuth2, JWT, mTLS, and API key schemes then dynamically manages token generation, injection, and renewal. Tests run with valid, up-to-date credentials, so nothing is skipped due to auth failures.
How is Levo different from SAST/DAST/WAF tools?
SAST checks source code but misses runtime context
DAST scans from the outside but fails on internal or dynamic APIs
WAFs only block edge traffic after deployment
Levo, in contrast, continuously tests every API with real payloads, role mapping, and behavior-driven exploits pre-production and post-deployment.
Does Levo reduce false positives?
Yes. Levo only surfaces exploited vulnerabilities validated by real traffic and behavior. Every finding includes a reproducible payload, test trace, and exploit context—so developers can fix with confidence.
How often does Levo run security tests?
Continuously. Levo runs on every code push, integration, or API change. No need to wait for quarterly scans your security posture evolves as fast as your APIs do.
Can Levo simulate role-based attacks like BOLA or IDOR?
Absolutely. Levo maps traffic to user roles, scopes, and sessions then simulates vertical and horizontal privilege escalations like BOLA, IDOR, and Broken AuthZ with precision and depth.
Will Levo slow down our release pipelines?
Not at all. Levo is CI/CD-native and designed to run in parallel, not in the way. You get full security coverage with zero delays, blocking only when critical, real-world risks are detected.
Show more