Runtime API Protection Without the Trade‑Offs


%20(1).png)









%20(1).png)







When API Protection Misfires,
Availability, Revenue, and Trust Take the Hit

Overly aggressive rule sets routinely stop legitimate API calls; studies show nearly half of WAF deployments run in “log only” mode because teams are afraid to block.

Signature-based approaches don’t catch business-logic abuse or obfuscated payloads. In one comparison, a leading WAF missed 88 % of real attacks.

Old proxy models fail closed or fail open, turning the blocker into a single point of failure. Latency compounds at scale, and downtime becomes another business risk.

Large rule sets and payload limits add tens of milliseconds of delay and can drop requests entirely, degrading the API experience customers depend on.

Perimeter WAFs only watch north–south traffic, leaving east–west microservice calls invisible. Attackers exploit these blind spots or hide payloads beyond scanning limits.

Vendor-managed signatures output thousands of untunable alerts. Teams spend months “tuning the box” instead of protecting APIs.
Inline Control Without Legacy Trade‑Offs
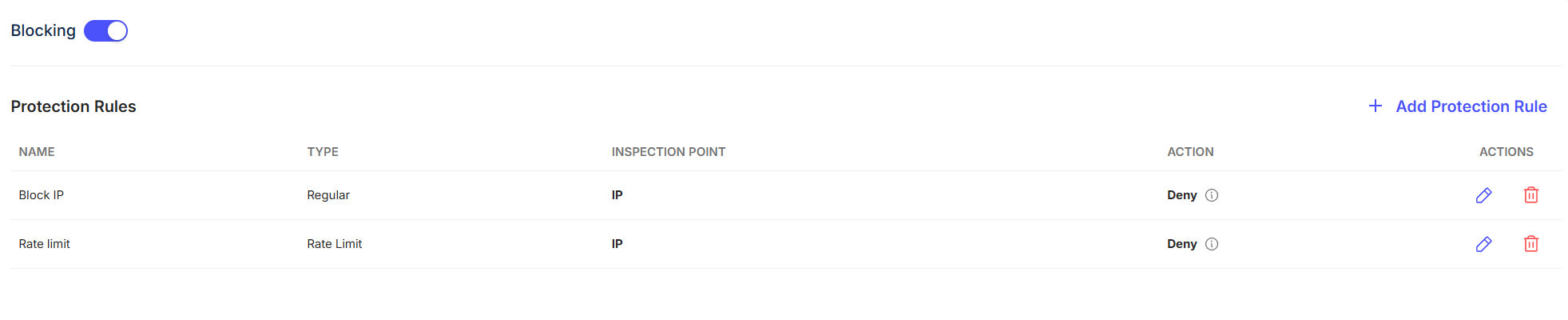
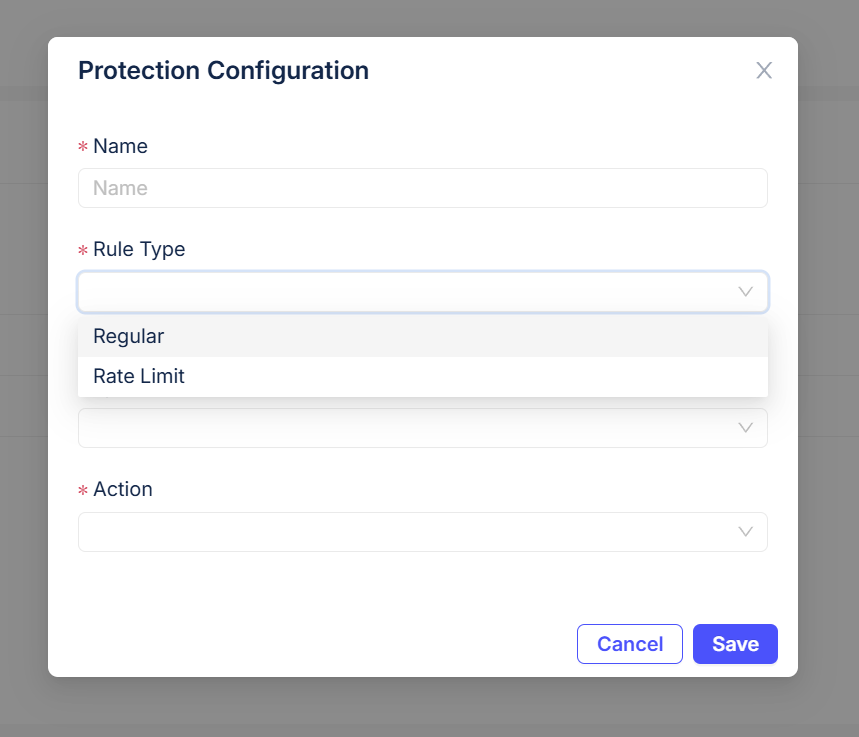
Precision blocking with white‑box rules
Replace opaque, vendor‑managed rules with a transparent engine. Levo ships curated base policies and lets you author or approve your own. Every decision is explainable and tunable, driving high true‑positive rates without sacrificing user experience.
Sub‑millisecond overhead, built for resilience
Levo’s protection module is stateless and engineered for single‑digit milliseconds of latency. It scales with your traffic and avoids the fail‑open/fail‑closed scenarios that cause outages.
Local analysis and zero egress
Traffic is processed by the Levo Satellite inside your environment, so sensitive payloads never leave your network. You avoid multi‑hundred‑thousand‑dollar egress bills and data‑residency concerns while retaining rich analysis.
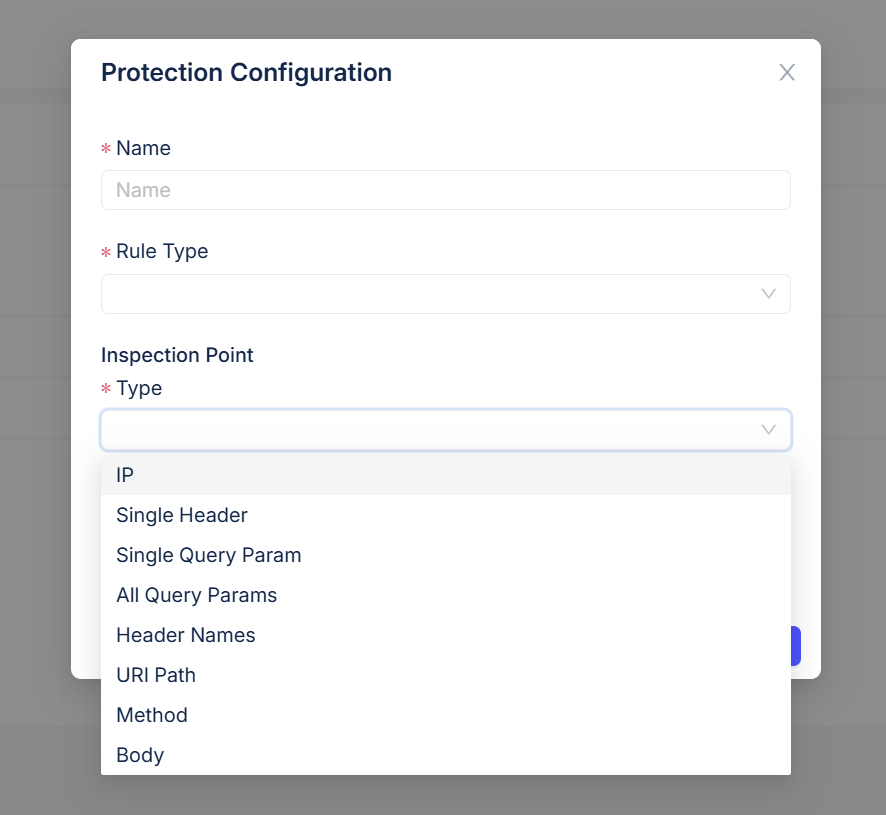
Full‑surface protection
Built on your API inventory and documentation, Levo protects new endpoints the moment they go live. Kernel‑level sensors monitor east‑west as well as north‑south traffic, so internal API calls and microservice communications are covered.
Adaptive protection that learns
Attack patterns observed by detection are turned into new test cases and proposed as temporary shielding. You can simulate and deploy these rules in minutes, staying ahead of attackers.

Block Real Threats Without Breaking Teams

Ship without second‑guessing. Transparent, precise rules mean your releases won’t be blocked by false positives.

Secure more with less. High‑fidelity, explainable enforcement eliminates triage overhead, letting lean teams focus on remediation.

Prevent incidents instead of reporting on them. Local enforcement and audit‑ready evidence reduce breaches and prevent incident response.
Stop attacks, not customers. Sub‑millisecond protection, zero data egress.

Frequently Asked Questions
Got questions? Go through the FAQs or get in touch with our team!
How is Levo’s API Protection different from traditional WAFs?
Unlike black-box, signature-driven WAFs, Levo enforces transparent white-box rules built on runtime API visibility. This prevents false blocks, sub-ms latency, and costly downtime.
Does API Protection add latency to customer-facing APIs?
No. Levo’s inline module runs with sub-millisecond overhead. It avoids fail-open/fail-closed bottlenecks and scales resiliently with traffic
How does Levo protect internal microservices and east-west traffic?
Levo’s kernel-level sensors extend beyond north-south perimeter monitoring, covering microservice calls, partner APIs, and newly deployed endpoints the moment they go live.
Can Levo prevent compliance and cost risks tied to off-box analysis?
Yes. All traffic is analyzed locally by Levo Satellites, so no payloads leave your environment. This eliminates multi-hundred-thousand-dollar egress bills and ensures data residency compliance
How is Levo’s Protection different from signature-based WAFs?
Levo uses transparent, tunable white-box rules built from runtime context, not opaque vendor-managed signatures. This means fewer false blocks and more trust.
Does API Protection add overhead to API latency?
No. Levo runs inline with sub-millisecond overhead, ensuring user experience and performance are never compromised.
How does Levo avoid false blocks?
Because enforcement is built on runtime API context and identity, Levo distinguishes valid calls from real exploits, preventing costly interruptions.
Does Levo’s Protection cover east–west traffic?
Yes. Unlike perimeter-only WAFs, Levo secures microservices, service mesh calls, and internal APIs in distributed environments.
How does Levo’s Protection support compliance needs?
By blocking real exploits before escalation, Levo reduces incident-response cycles and provides evidence that critical APIs are protected continuously.
Can Levo Protection run in hybrid or multi-cloud environments?
Yes. Satellites can be deployed across on-prem, cloud, and hybrid setups, ensuring consistent enforcement without central bottlenecks.
How does Levo prevent egress cost spikes in Protection?
All analysis happens locally within customer environments, avoiding the massive egress bills that come from shipping traffic to vendor clouds for inspection.
Can Levo Protection scale with API-first enterprises?
Yes. Protection is architected for resilience at scale, handling high traffic volumes across thousands of APIs with sub-ms latency.
Does Levo Protection integrate with developer workflows?
Yes. Block events and remediation details flow directly into existing dev workflows like Jira and Slack, ensuring rapid fix cycles.
How does Levo Protection reduce security team burnout?
By blocking only real exploits and avoiding noise, Levo prevents wasted cycles on false positives—allowing lean teams to stay focused and effective.
Show more