Secure API data sharing


%20(1).png)









%20(1).png)







APIs are the new lifelines for healthCare,
Levo keeps them secure by default
Proactively protect patient data and prevent HIPAA violations
Levo automatically identifies every API handling PHI or PII and ensures continuous encryption and strong access controls. So patient records shared across EHR systems remain protected whether accessed internally or by third parties.
Achieve CMS compliance without shipping insecure APIs
Meet CMS Interoperability deadlines with confidence by proactively securing every FHIR API. Even in legacy systems, Levo continuously inventories, documents, tests and monitors APIs so compliant app-based access is provided without exposing patient data.
Drive revenue by securing the APIs patients depend on
Levo secures the APIs that connect your healthcare databases to mobile apps, IoMT devices, and public health systems so you can grow market share and revenue through rapid and safe data sharing.
Digitize without delay even with legacy systems
Fight Technical debt through rapid and secure API Adoption even in environments weighed down by siloed, outdated systems. By automating API inventory, documentation, and testing, Levo eliminates the friction and risk that typically slows down API-led digitization initiatives.
Eliminate breach risks from third party integrations
Whether it’s a cloud-hosted mHealth app or a FHIR-enabled claims processor, Levo ensures patient data isn’t exposed through fast-moving, often unvetted integrations. Achieve automatic and continuous insight into all the partner, third-party and open source APIs.

Don’t lose patients to
poor data sharing or security incidents
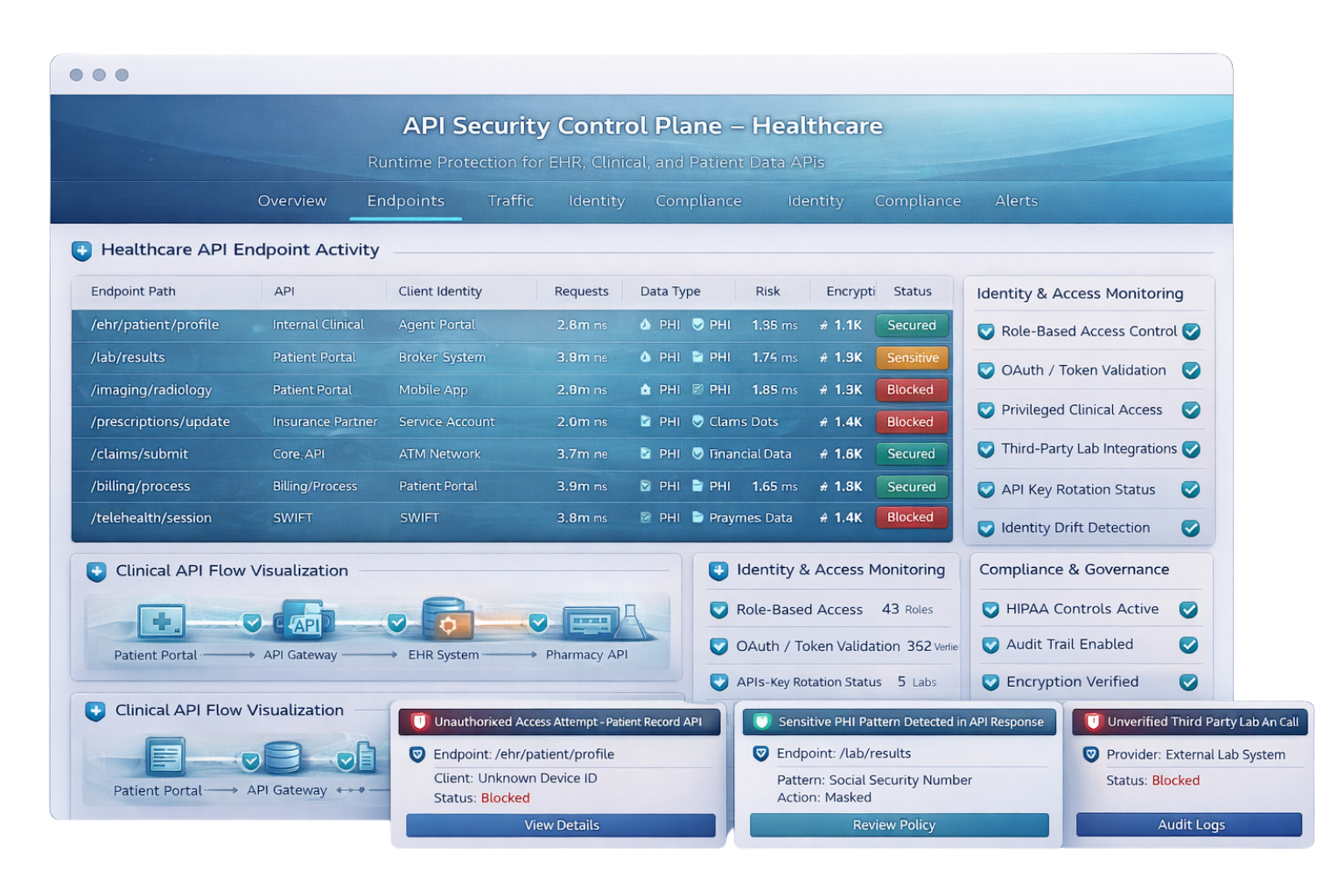
Live API inventory for EHRs, partners, and shadow integrations
Levo’s eBPF-powered discovery engine creates a real-time inventory of every API: internal, third-party, open source, and orphaned across environments.
In a healthcare setting, this means finding FHIR APIs that grant access to EHR data, IoT APIs syncing telemetry from medical devices, and even forgotten scheduling APIs still integrated into front-end apps.
No code changes or config rewrites are required to give security and compliance teams the live catalog they’ve always needed.
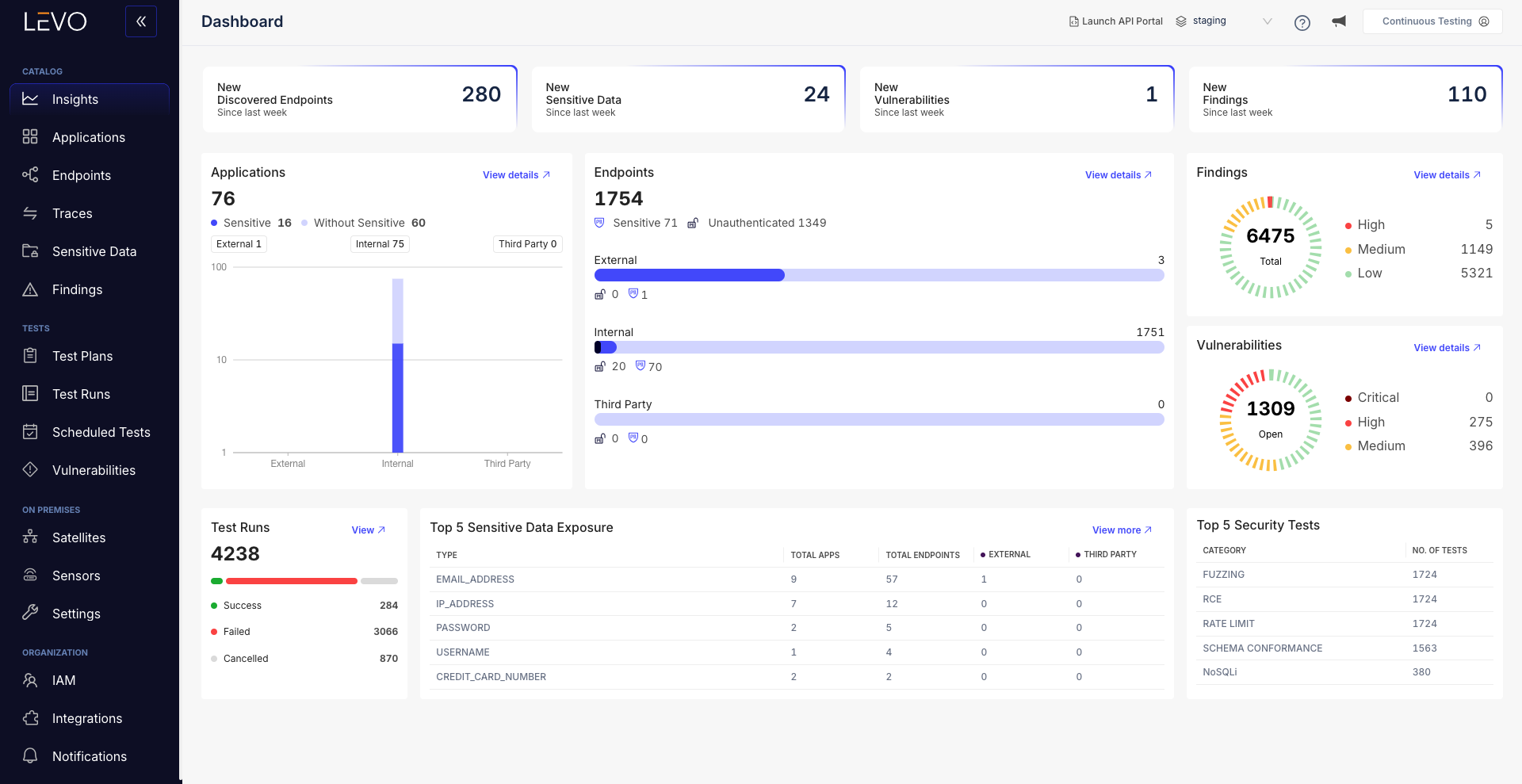
Autogenerated API documentation for audit readiness and testing
Every discovered API is automatically documented with 12+ parameters, including methods, response types, data formats, rate limits, human-readable description and auth logic.
Security and compliance teams understand each API’s purpose, expected behavior, and exposure profile.
This documentation makes endpoints testable, observable, and audit-ready without needing developers to work on non revenue generating activities.
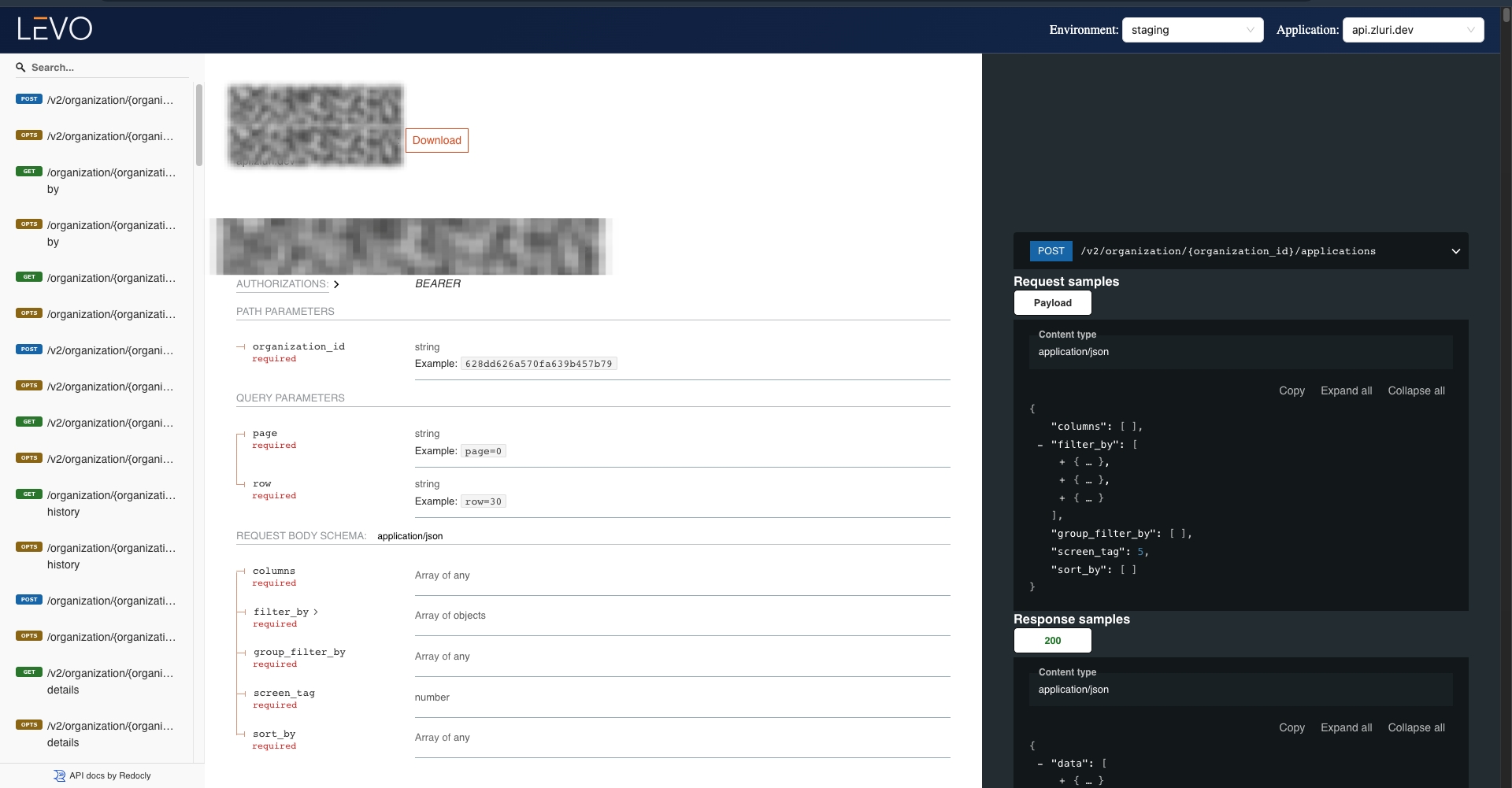
Sensitive data classification for PHI and PII
Levo continuously inspects API traffic and classifies all sensitive data flowing through endpoints, including PHI, insurance numbers, login credentials, and consent forms.
It flags any API touching sensitive data that lacks authentication, proper encryption (e.g., TLS 1.3), or fine-grained access controls.
Compliance teams align APIs as HIPAA safeguards, and security teams prioritize enforcement not by guesswork, but through proof.

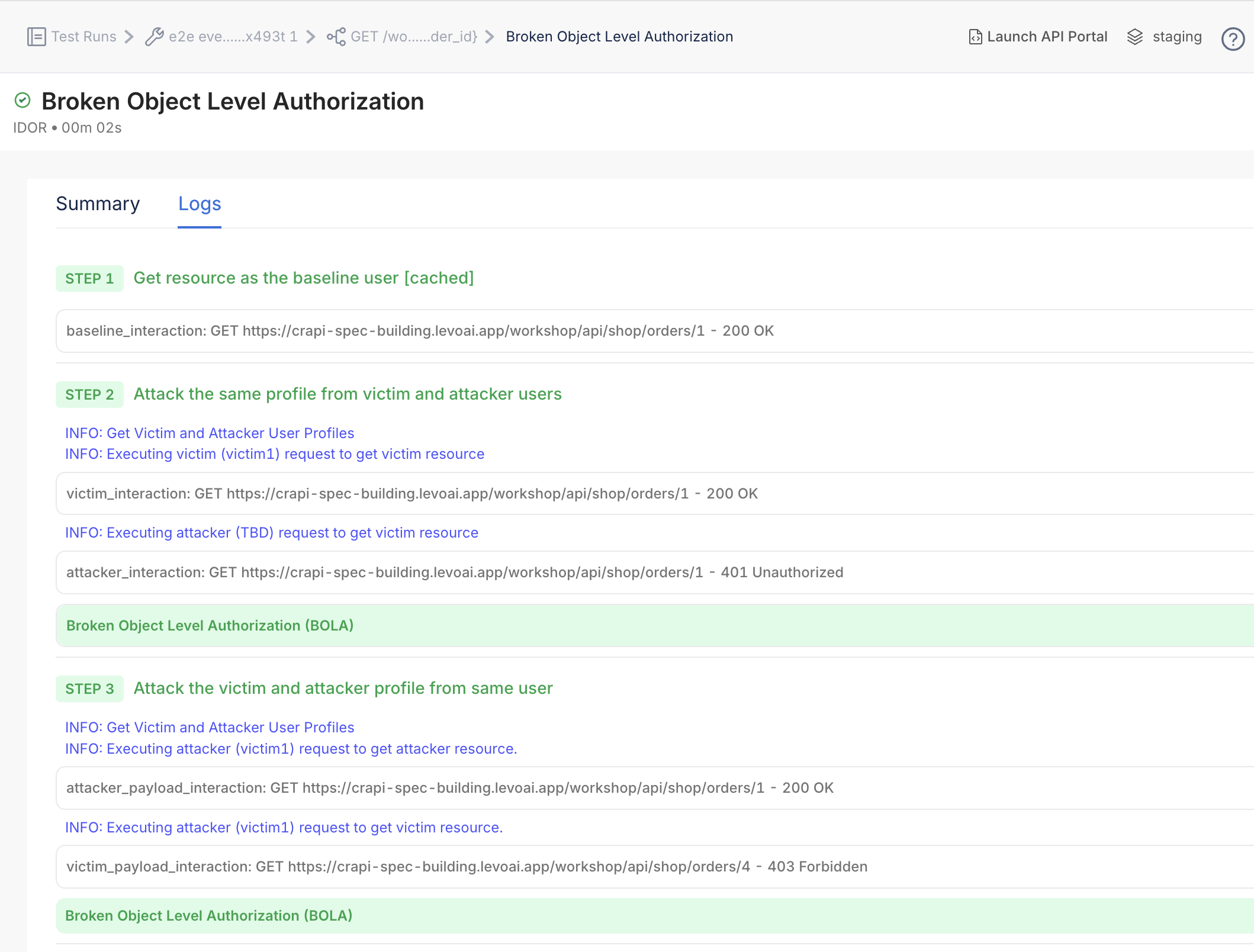
Security testing that runs in CI/CD and maps to real-world threats
Levo simulates real-world attacks against every endpoint using custom, context-aware payloads that reflect how healthcare APIs are actually used.
It covers OWASP API Top 10 risks, object-level authorization bypasses, broken token flows (OAuth2.0, OpenID Connect), SQL injection paths, verbose error responses, and more.
All tests run inline in CI/CD pipelines, supporting rapid deployments and secure-by-default SDLC workflows.
Detects misconfigurations, drift, and anomalies before a breach reveals them
Levo continuously monitors API behavior and flags anything that deviates from expected baselines across all environments.
It surfaces over 50 misconfiguration types out of the box and supports custom policy rules tailored to healthcare-grade enforcement requirements.
Patient data access to move both treatment and trust forward




