Cut both app delivery time and security risks in half


%20(1).png)









%20(1).png)







60% of breaches happen through unpatched vulnerabilities, not zero-days.

Nearly a third of teams say the majority of scanner findings are false positives. GitLab’s 2024 DevSecOps report ranked this as the second most frustrating challenge for security teams. The result? Burnout, backlog bloat, and dev teams who stop trusting the tools entirely.

55% of organizations lack a unified prioritization model, and 37% cite poor context as the biggest blocker to action. When alerts lack exploit context, reachability insight, or business impact mapping, they all blur into static. Critical issues remain untouched—not because they’re hard to fix, but because no one can prove they’re real.

Security teams still manually assign vulnerabilities through Excel, chase updates via DMs, and dump generic tickets into Jira. No reproduction payloads. No API context. No owner. So devs snooze the alerts or worse, ignore them altogether.

57% of security teams spend up to half their time manually consolidating and normalizing findings from legacy tools: SAST, DAST, SCA, WAF all in different formats, none with complete application and runtime context.

68% of enterprises take more than 24 hours just to begin remediation. The average time to fully patch a critical issue? 4.5 months. In some cases, 9+. Meanwhile, attackers exploit the known and exposed. And teams continue patching blind, not smart.
Move from detection to resolution
Levo knows who should fix, what, how and why
Eliminate false positives with payloads that mirror real-world attack patterns
Levo only surfaces vulnerabilities that have already been exploited, validated using live traffic, real user data and authenticated sessions.
No vulnerability backlogs. Just a short list of vulnerabilities your team can trust, act on, and verify in seconds. Because every ticket includes a replayable payload, exploit context, and traces so developers aren’t left guessing what broke or why it matters.
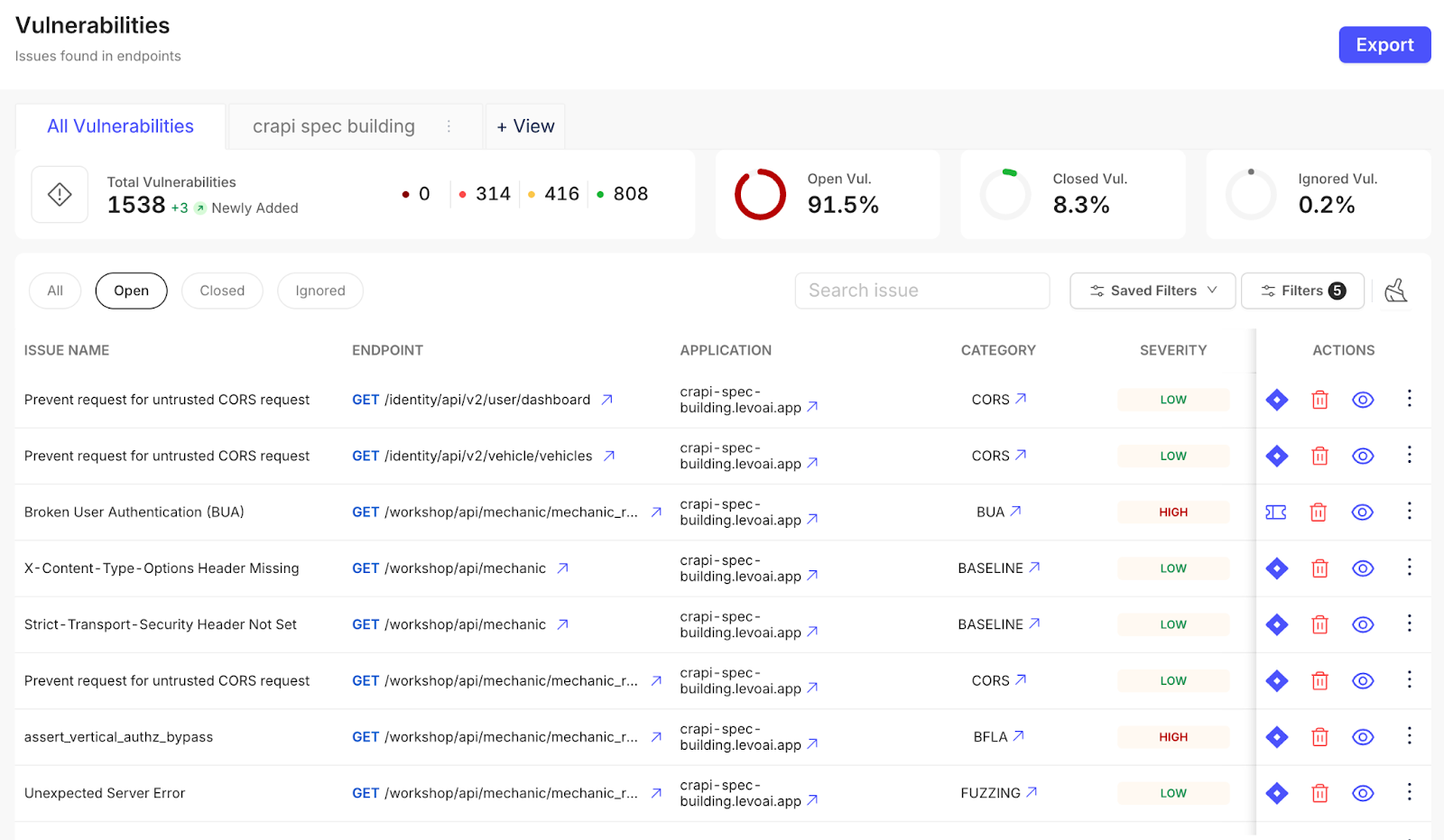
End manual triage forever with true remediation automation
57% of security teams spend up to half their week just triaging vulnerabilities normalizing outputs, assigning owners, and rewriting alerts. Levo automates all of it.
From exploit to engineer, everything is handled: vulnerability detection, payload reproduction, dev/service mapping, and ticket creation.
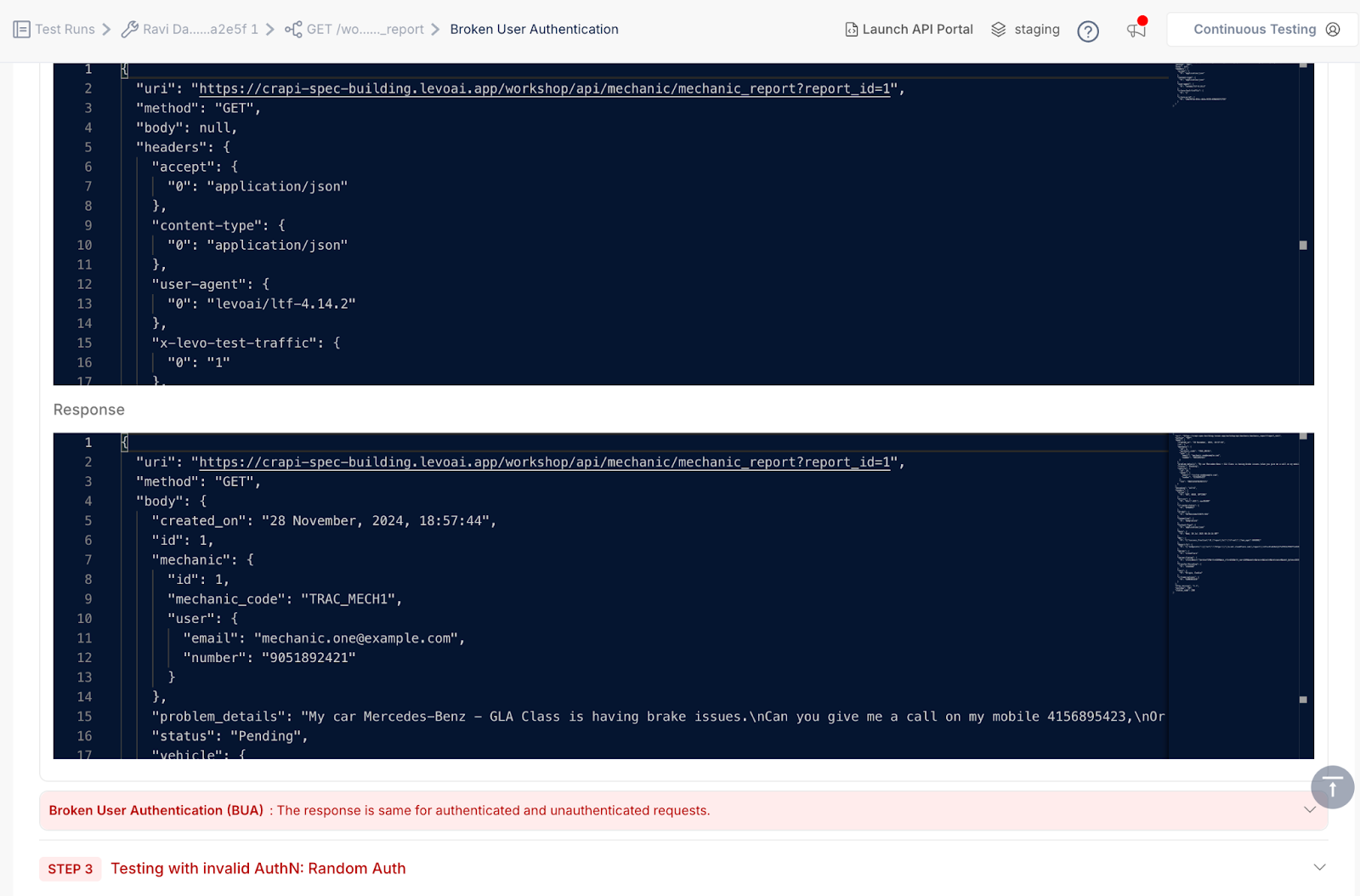
Prioritize what matters most based on live data, not static severity
37% of security teams cite poor context as their biggest blocker to prioritization. Levo solves this by layering real-time insights like sensitive data exposure, endpoint type (internal, external, or partner), traffic patterns, and authentication scheme.
The result?
Issues tied to external-facing endpoints, payment flows, or high-sensitivity data automatically float to the top, so security and engineering align on what matters most.
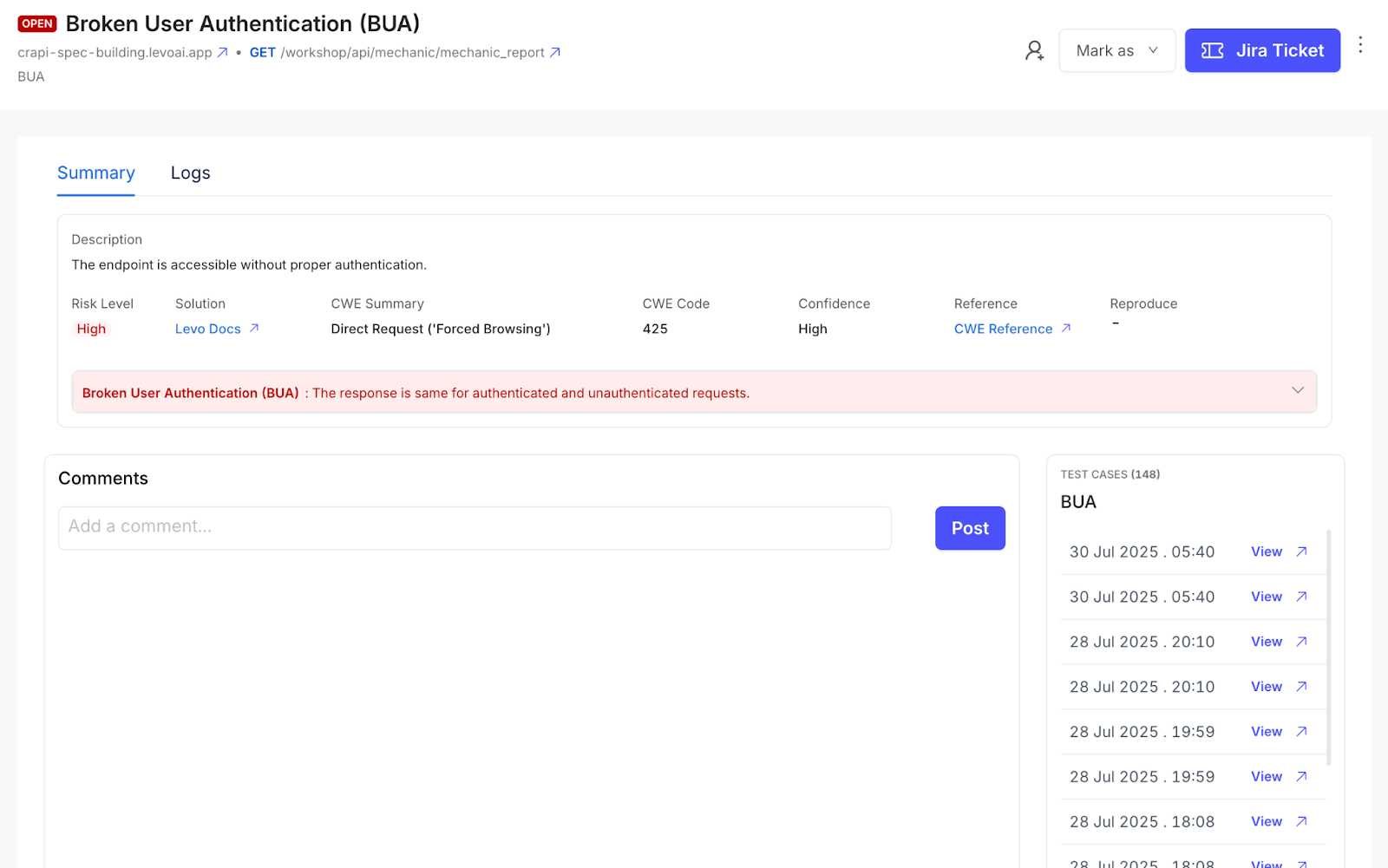
Insights over alerts, so every team moves faster

More fixes happen faster. Vulnerabilities come with surrounding API context, reproduction payloads, and clear ownership. No more guessing severity or root cause.

Stop chasing false positives or triaging tickets manually. Focus only on vulnerabilities already exploited with mapped ownership and prioritized risk.

Track remediation progress with real, runtime-validated evidence. Every fix comes trace-linked and timestamped ready for audits without extra effort.
Vulnerability management that moves security posture forward, not just alert count

Frequently Asked Questions
Got questions? Go through the FAQs or get in touch with our team!
Can Levo validate whether a fix worked?
Yes. Levo continuously re-tests APIs using exploit-aware payloads mapped to live traffic. Once a vulnerability is marked fixed, Levo automatically re-validates the endpoint in subsequent CI/CD cycles and runtime flows. If the vulnerability persists, it resurfaces with updated payloads and context, closing the loop with continuous validation, not one-time confirmation.
Do developers need to log into Levo to view issues?
No. Levo pushes enriched, replayable vulnerability findings directly into developer workflows Jira, GitHub, Slack, Teams with full context, including the affected API, environment, request/response traces, and reproduction payloads. Developers resolve issues where they already work, without toggling between dashboards.
Can I assign issues to specific teams or services?
Yes. Levo automatically maps vulnerabilities to the responsible API, environment, and developer using endpoint-level metadata and repository ownership. You can define assignment rules by service, team, or environment ensuring the right engineer gets the right issue without manual triage or context loss.
Does Levo integrate with our current CI/CD?
Absolutely. Levo natively integrates with modern CI/CD pipelines including GitHub Actions, GitLab CI/CD, Jenkins, CircleCI, and Bitbucket. It can trigger security tests pre-merge, post-deploy, or on a schedule validating new API behavior and confirming fixes without slowing releases.
What is API Inventory?
API Inventory is a real-time catalog of every API your organization runs internal, external, shadow, or third-party across all environments. It’s foundational for securing, monitoring, and governing API behavior at scale.
What is Vulnerability Management?
Vulnerability Management is the process of identifying, prioritizing, and remediating security flaws in software systems. For APIs, this includes misconfigurations, broken authentication, data exposure, and logic-layer vulnerabilities.
Why is Vulnerability Management important?
Over 60% of breaches come from unpatched vulnerabilities, not zero-days. Managing them effectively prevents incidents, reduces compliance risk, and strengthens your security posture while protecting delivery velocity.
How is Levo better than other solutions available in the industry?
Levo surfaces only exploited vulnerabilities, not static scan noise. It adds runtime context, ownership mapping, and replayable payloads so teams know what to fix, why it matters, and who owns it. Most tools stop at detection and Levo starts at resolution.
How does Levo reduce false positives?
Levo validates vulnerabilities through live, runtime-executed payloads based on actual API usage. Only real, reproducible issues reach your backlog so teams stop wasting time on theoretical or duplicate alerts.
Will Levo slow down our CI/CD pipelines?
No. Levo is built for modern CI/CD. It runs parallel, non-blocking API tests using 1000+ exploit-aware payloads and requires zero code changes ensuring security keeps up with your delivery speed.
Can Levo show who owns the vulnerability?
Yes. Every surfaced vulnerability is automatically mapped to the responsible developer, service, or team so remediation isn't just fast, it’s correctly routed with zero manual triage.
How is remediation automated in Levo?
Levo automates everything from exploit validation to Jira ticket creation embedding payloads, traces, and context directly into workflows. Developers get ready-to-fix tickets, not just red flags.
Does Levo track if vulnerabilities are actually fixed?
Yes. Levo continuously tests in runtime and pre-production. Once a vulnerability is remediated, Levo validates the fix and updates the remediation status so you close the loop and pass audits effortlessly.
What kind of vulnerabilities does Levo detect?
Levo detects critical API-layer vulnerabilities like AuthZ failures (BOLA/BFLA), injection flaws, data exposure, broken session management, insecure object references, and configuration weaknesses all validated in real runtime.
Does Levo integrate with our existing security stack?
Yes. Levo integrates with Jira, Splunk, Slack, Teams, and more. Its outputs can also be consumed by your SIEM, SOAR, and ticketing tools, ensuring alignment across security and engineering.
What makes Levo different from traditional API security scanners?
Unlike traditional SAST/DAST/SCA tools that flood you with theoretical issues, Levo surfaces only exploited, runtime-validated vulnerabilities so your teams fix what’s real, not chase ghosts.
How does Levo reduce false positives?
Levo replays real-world attack paths observed in live traffic, using authenticated sessions and actual payloads. This eliminates guesswork and ensures every surfaced issue is reproducible and provably exploitable.
Will Levo slow down our CI/CD pipelines?
Not at all. Levo runs lightweight, context-aware tests in parallel or on-demand pre-merge or post-deploy so you get fast, accurate security feedback without delaying releases.
Can Levo show who owns the vulnerability?
Yes. Levo auto-maps every issue to the responsible API, environment, and code owner using repo metadata and runtime traces. No more Slack threads or manual assignments.
How is remediation automated in Levo?
Every surfaced issue includes replayable payloads, impacted API details, and suggested fixes—auto-exported to Jira, GitHub, Slack, or Teams. Levo handles triage so your team focuses only on fixing.
Does Levo track if vulnerabilities are actually fixed?
Yes. After a fix, Levo continuously re-tests the same exploit path across CI/CD and runtime environments. If it’s still exploitable, it resurfaces, closing the loop with continuous validation.
What kind of vulnerabilities does Levo detect?
Levo targets real-world API abuse: broken auth, excessive data exposure, injection flaws, BOLA, misconfigured endpoints, and more prioritized by exploitability and business impact.
Show more